Silent Mode Installation
This procedure documents installation for Platform Analytics, release 9.3. If you need installation information for one of the following earlier releases, use the links below to open earlier PDF installation guides maintained on the PTC eSupport Portal:
Silent mode installation of Platform Analytics is supported for the Linux environment. In contrast to the graphical and text modes, where the installation proceeds through a series of interactive steps, the silent installation requires that all of the necessary input be included in the launch command. The installation then takes place with no further interaction required.
Before Installation
• Make sure all of the prerequisites have been met.
• Download the appropriate installer files for your operating system.
• Extract the downloaded files to a location on your host system.
• If you plan to use an existing external instance of RabbitMQ or Apache Flink, instead of installing the components provided with the installer, those servers must be running during the Platform Analytics installation.
• If you plan to use TLS support for connections to any Platform Analytics components, review and complete any necessary tasks in the following sections:
|
|
For Platform Analytics 9.2 and earlier, the TLS installation parameters must still use SSL instead of TLS.
|
Installation Launch Command
To launch the silent installation in a Windows environment, open the Windows PowerShell (or the Command Prompt window) in Administrator mode and navigate to the directory where you saved the extracted launch files.
Run a launch command, similar to the example below. Substitute specific information in the angled brackets. For information about each set of command parameters, expand the relevant links below to view the detailed tables.
|
|
If you enter true to enable TLS for ThingWorx, RabbitMQ, or Flink, several additional command parameters are required. For information about those parameters, see the relevant sections below.
|
.\PlatformAnalytics-<n.n.n>-windows-installer.exe ^
--unattendedmodeui minimal ^
--mode unattended ^
--accept_eula YES ^
--baseinstalldir "<base installation directory>" ^
--THINGWORX_FOUNDATION_IP_ADDR "<IP address or host name>" ^
--THINGWORX_FOUNDATION_PORT "<Port where ThingWorx is running>" ^
--THINGWORX_APPKEY "<valid ThingWorx App Key>" ^
--USE_TLS <false/true> ^
--RABBIT_MQ_USER_NAME_NEW "<user name>" ^
--RABBIT_MQ_PASSWORD_NEW <password> ^
--RABBITMQ_TLS <true/false> ^
--RABBITMQ_TLS_EXISTING <true/false> ^
--FLINK_TLS_NEW <true/false> ^
--FLINK_TLS_EXISTING <true/false> ^
--unattendedmodeui minimal ^
--mode unattended ^
--accept_eula YES ^
--baseinstalldir "<base installation directory>" ^
--THINGWORX_FOUNDATION_IP_ADDR "<IP address or host name>" ^
--THINGWORX_FOUNDATION_PORT "<Port where ThingWorx is running>" ^
--THINGWORX_APPKEY "<valid ThingWorx App Key>" ^
--USE_TLS <false/true> ^
--RABBIT_MQ_USER_NAME_NEW "<user name>" ^
--RABBIT_MQ_PASSWORD_NEW <password> ^
--RABBITMQ_TLS <true/false> ^
--RABBITMQ_TLS_EXISTING <true/false> ^
--FLINK_TLS_NEW <true/false> ^
--FLINK_TLS_EXISTING <true/false> ^
|
|
If you have deployed ThingWorx in a cluster configuration, and you plan to implement Anomaly Detection, you must add an enable–components parameter to the above launch command with additional Analytics Server connection information. For a description of the enable–components parameter and connection information, see Enabling Anomaly Detection in a ThingWorx Cluster
|
Installation Directory
Launch Command Parameter | Description | ||
|---|---|---|---|
--baseinstalldir | The path to the directory where Platform Analytics will be installed.
|
ThingWorx Connection Information
Launch Command Parameter | Description | ||||
|---|---|---|---|---|---|
--THINGWORX_FOUNDATION_IP_ADDR | IP address or host name of your ThingWorx server, which must already be installed and running. If you are using TLS for your connection to ThingWorx, this IP Address or Host Name must match the SAN address or host used to create the ThingWorx TLS certificate. | ||||
--THINGWORX_FOUNDATION_PORT | The port for communicating with your ThingWorx server. If you are using TLS for your connection to ThingWorx, enter that port number. | ||||
--THINGWORX_APPKEY | The value from the Key ID field of the application key you created in ThingWorx. | ||||
--USE_TLS
| Set to true in order to require the use of TLS when connecting to ThingWorx. The default value is false.
| ||||
--UPLOAD_THINGWORX_CERTIFICATE_FILE |
Set to true if you want the installer to upload your ThingWorx TLS certificate automatically. The default value is false For a new installation using TLS, this option must be enabled. For an upgrade, modify, or repair installation, this option is necessary only if you want to upload a new certificate. To continue using an existing certificate, use the default value (false). For more information, see TLS Support for ThingWorx. | ||||
--THINGWORX_CERTIFICATE_FILE |
Path to the TLS certificate created for your ThingWorx server. This parameter is required when --UPLOAD_THINGWORX_CERTIFICATE_FILE is set to true. | ||||
--THINGWORX_TRUSTSTORE_PASSWORD_PARAM |
Enter a password that will be assigned to the ThingWorx truststore. This truststore will be created automatically during the Platform Analytics installation. |
RabbitMQ Configuration Information
Both the --RABBITMQ_TLS and the --RABBIT_MQ_TLS_EXISTING parameters are required in the launch command, whether installing the new RabbitMQ instance that comes with the installer or pointing to an existing instance, and whether TLS is enabled or not. To understand what these parameters mean and how to set them for each scenario, see the following table. 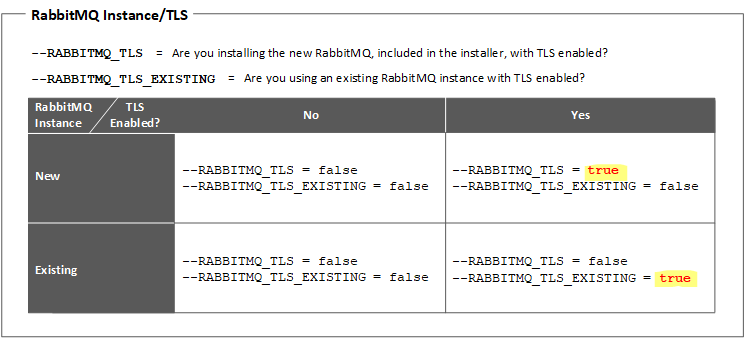 |
Scenario | Launch Command Parameters | ||
|---|---|---|---|
Without TLS
| • --RABBIT_MQ_USER_NAME_NEW – User name for the RabbitMQ component. • --RABBIT_MQ_PASSWORD_NEW – Password for the RabbitMQ component. Will be encrypted automatically as part of the installation process. • --RABBITMQ_TLS – Set to false to disable TLS. • --RABBIT_MQ_TLS_EXISTING – Set to false to indicate that you are not using an existing RabbitMQ instance with TLS enabled. The RabbitMQ virtual host is set to the root directory by default: “/” | ||
With TLS
| • --RABBIT_MQ_USER_NAME_NEW – User name for the RabbitMQ component. • --RABBIT_MQ_PASSWORD_NEW – Password for the RabbitMQ component. Will be encrypted automatically as part of the installation process. • --RABBITMQ_TLS – Set to true to enable TLS. • --RABBIT_MQ_TLS_EXISTING – Set to false to indicate that you are not using an existing RabbitMQ instance with TLS enabled. • --RABBITMQ_CA_FILE_PATH – Path to the RabbitMQ CA Bundle file, ca_certificate.pem. Must contain the authority that signed the RabbitMQ certificate. If using TLS for the connection between RabbitMQ and ThingWorx, this bundle must also include the authority that signed the Thingworx certificate. • --RABBITMQ_CERT_FILE_PATH – Path to the RabbitMQ Certificate file, rabbitmq_certificate.pem. • --RABBITMQ_KEY_FILE_PATH – Path to the corresponding RabbitMQ Key file, rabbitmq_key.pem. • Truststore information as following: ◦ For 9.2 and later – --RABBITMQ_TRUSTSTORE_PASSWORD – Enter a password that will be assigned to the RabbitMQ truststore. This truststore will be created automatically during the Platform Analytics installation. ◦ For 9.0 and 9.1 – --RABBITMQ_CA_ALIAS_NAME – Alias name assigned to the RabbitMQ certificate for importing into the Java truststore. Alias names are converted automatically to all lower case. --SERVER_TRUSTSTORE_PASSWORD – Password for the Java truststore. The truststore is created automatically, with a default password, when Java is installed. For more information about Java Truststore passwords, see Working with Certificates and SSL on the Oracle website. • --CLIENT_PKCS12_FILE_PATH – Path to the Property Transform PKCS12 file, client.pkcs12, containing a certificate and the corresponding key. It must be signed by an authority in the RabbitMQ CA Bundle. To create the PKCS12 file, use the OpenSSL tool. For example: openssl pkcs12 -export -in <certificate.pem> -inkey <key.pem> -out client.pkcs12 • --CLIENT_PKCS12_PASSWORD – An optional password for the PKCS12 file. The RabbitMQ virtual host is set to the root directory by default: “/” |
Launch Command Parameter | Description | ||
|---|---|---|---|
Without TLS
| • --disable-components rabbit_mq – A parameter that prevents the RabbitMQ instance provided with the installer from installing. • --RABBIT_MQ_USER_NAME – A user name for the existing RabbitMQ component. • --RABBIT_MQ_PASSWORD – A password for the existing RabbitMQ component. The password will be encrypted automatically as part of the installation process. • --RABBIT_MQ_IP_ADDR – A RabbitMQ IP address or host name. • --RABBIT_MQ_PORT_EXISTING – A port where RabbitMQ is running. • --RABBIT_MQ_VIRTUALHOST – A virtual host for the existing RabbitMQ. • --RABBITMQ_TLS – Set to false to indicate that you are not using a new RabbitMQ instance with TLS enabled. • --RABBIT_MQ_TLS_EXISTING – Set to false to indicate that you are not using an existing RabbitMQ instance with TLS enabled. | ||
With TLS
| • --disable-components rabbit_mq – A parameter that prevents the RabbitMQ instance provided with the installer from installing. • --RABBIT_MQ_USER_NAME – A user name for the existing RabbitMQ component. • --RABBIT_MQ_PASSWORD – A password for the existing RabbitMQ component. The password will be encrypted automatically as part of the installation process. • --RABBIT_MQ_IP_ADDR – A RabbitMQ IP address or host name. • --RABBIT_MQ_PORT_EXISTING – A port where RabbitMQ is running. • --RABBIT_MQ_VIRTUALHOST – A virtual host for the existing RabbitMQ. • --RABBITMQ_TLS – Set to false to indicate that you are not installing a new instance of RabbitMQ with TLS enabled. • --RABBIT_MQ_TLS_EXISTING – Set to true to indicate that you are using an existing RabbitMQ instance with TLS enabled. • --RABBIT_MQ_TLS_CLIENT_STORE – Path to the Property Transform PKCS12 file, client.pkcs12, containing a certificate and the corresponding key. It must be signed by an authority in the RabbitMQ CA Bundle. To create the PKCS12 file, use the OpenSSL tool. For example: openssl pkcs12 -export -in <certificate.pem> -inkey <key.pem> -out client.pkcs12 • --RABBIT_MQ_TLS_CLIENT_STORE_PASSWORD – An optional password for the PKCS12 file. • --RABBIT_MQ_TLS_SERVER_TRUST_STORE – Path to a JKS Truststore file that contains the authority that signed the RabbitMQ certificate. • --RABBIT_MQ_TLS_SERVER_TRUST_STORE_PASSWORD – Password for the TLS Truststore. For more information about Java Truststore passwords, see Working with Certificates and SSL on the Oracle website. |
Flink Configuration Information
Both the --FLINK_TLS_NEW and the --FLINK_TLS_EXISTING parameters are required in the launch command, whether installing the new Flink instance that comes with the installer or pointing to an existing instance, and whether TLS is enabled or not. To understand what these parameters mean and how to set them for each scenario, see the following table. 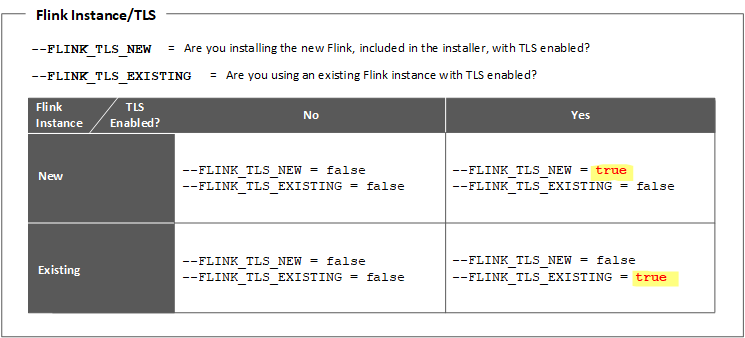 |
If you choose to disable TLS protection, you must block your Flink REST port (typically port 8086) via your firewall. Otherwise, the port will be exposed to outside networks. |
For more information about creating the appropriate certificates, see TLS Support for Flink.
Scenario
Launch Command Parameters
Flink REST – No TLS
For Platform Analytics 9.2 and earlier, continue to use SSL for all TLS parameters. |
• --FLINK_TLS_NEW – Set to false, to disable TLS.
• --FLINK_TLS_EXISTING – Set to false to indicate that you are not using an existing Flink instance with TLS enabled.
No additional parameters are required.
Flink REST – Yes TLS
For Platform Analytics 9.2 and earlier, continue to use SSL for all TLS parameters. |
• --FLINK_TLS_NEW – Set to true to enable TLS.
• --FLINK_TLS_EXISTING – Set to false to indicate that you are not using an existing Flink instance with TLS enabled.
• --FLINK_TLS_NEW_KEYSTORE – Path to the REST Keystore file where the signed Flink REST TLS certificate is stored. The file can be in JKS or PKCS12 format. The Flink REST certificate is used by the Flink REST endpoint.
• --FLINK_TLS_NEW_KEYSTORE_PASSWORD – Password for the Flink REST Keystore.
• --FLINK_TLS_NEW_KEY_PASSWORD – Password used to protect the private key of the REST Keystore. This key password was defined when the REST Keystore was created and may be the same as the Keystore Password.
• --FLINK_CLIENT_TLS_NEW_KEYSTORE – Path to the Client Keystore file where the signed Flink Client TLS certificate is stored. The file can be in JKS or PKCS12 format. The Flink Client certificate is used by the Flink client on the Property Transform microserver.
• --FLINK_CLIENT_TLS_NEW_KEYSTORE_PASSWORD – Password for the Flink Client Keystore.
• --FLINK_CLIENT_TLS_NEW_KEY_PASSWORD – Password used to protect the private key of the Client Keystore. This key password was defined when the Client Keystore was created and may be the same as the Keystore Password.
• --FLINK_TLS_NEW_TRUST_STORE – Path to a REST Truststore file that contains the certificate authority root that signed the Flink certificate. The file can be in JKS or PKCS12 format.
• --FLINK_TLS_NEW_TRUST_STORE_PASSWORD – Password for the Flink REST Truststore.
Flink Internal – No TLS
This scenario is not available in 9.2 and later. For earlier releases, this parameter will need to be added to the launch command. This parameter must continue to use SSL instead of TLS. |
--FLINK_SSL_INTERNAL – Set to false.
No additional parameters are required.
Flink Internal – Yes TLS
This scenario is not available in 9.2 and later. For earlier releases, these parameters will need to be added to the launch command. These parameters must continue to use SSL instead of TLS. |
• --FLINK_SSL_INTERNAL – Set to true.
• --FLINK_SSL_INTERNAL_KEYSTORE – Path to the Internal Keystore file where the signed Flink TLS certificate is stored. The file can be in JKS or PKCS12 format.
• --FLINK_SSL_INTERNAL_KEYSTORE_PASSWORD – Password for the Flink Internal Keystore.
• --FLINK_SSL_INTERNAL_TRUST_STORE – Same path as the Internal Keystore file, unless you created a separate Internal Truststore file. The file can be in JKS or PKCS12 format.
• --FLINK_SSL_INTERNAL_TRUST_STORE_PASSWORD – Same password as the Flink Internal Keystore, unless you created a separate Internal Truststore file.
• --FLINK_SSL_INTERNAL_KEY_PASSWORD – Password used to protect the private key of the Internal Keystore. This key password was defined when the Internal Keystore was created and may be the same as the Keystore Password.
If you choose to disable TLS protection, your Flink REST port will be exposed to outside networks. |
For more information about creating the appropriate certificate, see TLS Support for Flink.
Scenario
Description
Flink REST – No TLS
For Platform Analytics 9.2 and earlier, continue to use SSL for all TLS parameters. |
• --disable-components flink – A parameter that prevents the Flink instance provided with the installer from installing.
• --FLINK_IP_ADDR – IP address of an external Flink instance.
• --FLINK_PORT – Port where an external Flink instance is running.
• --FLINK_TLS_NEW – Set to false, to indicate that you are not installing a new Flink instance with TLS enabled..
• --FLINK_TLS_EXISTING – Set to false to indicate that you are not using an existing Flink instance with TLS enabled.
Flink REST – Yes TLS
For Platform Analytics 9.2 and earlier, continue to use SSL for all TLS parameters. |
• --disable-components flink – A parameter that prevents the Flink instance provided with the installer from installing.
• --FLINK_IP_ADDR – IP address of an external Flink instance.
• --FLINK_PORT – Port where an external Flink instance is running.
• --FLINK_TLS_NEW – Set to false, to indicate that you are not installing a new Flink instance with TLS enabled.
• --FLINK_TLS_EXISTING – Set to true to indicate that you are using an existing Flink instance with TLS enabled.
• --FLINK_TLS_EXISTING_KEYSTORE – Path to the REST Keystore file where the signed Flink TLS certificate is stored. The file can be in JKS or PKCS12 format.
• --FLINK_TLS_EXISTING_KEYSTORE_PASSWORD – Password for the Flink REST Keystore.
• --FLINK_TLS_EXISTING_KEY_PASSWORD – Password used to protect the private key of the REST Keystore. This key password was defined when the REST Keystore was created and may be the same as the Keystore Password.
• --FLINK_CLIENT_TLS_EXISTING_KEYSTORE – Path to the Client Keystore file where the signed Flink Client TLS certificate is stored. The file can be in JKS or PKCS12 format. The Flink Client certificate is used by the Flink client on the Property Transform microserver.
• --FLINK_CLIENT_TLS_EXISTING_KEYSTORE_PASSWORD – Password for the Flink Client Keystore.
• --FLINK_CLIENT_TLS_EXISTING_KEY_PASSWORD – Password used to protect the private key of the Client Keystore. This key password was defined when the Client Keystore was created and may be the same as the Keystore Password.
• --FLINK_TLS_EXISTING_TRUST_STORE – Path to a REST Truststore file that contains the authority that signed the Flink certificate. The file can be in JKS or PKCS12 format.
• --FLINK_TLS_EXISTING_TRUST_STORE_PASSWORD – Password for the Flink REST Truststore.
Running the Installation
By default, when the installer runs, all Platform Analytics components are included in the silent mode installation, including the RabbitMQ and Flink components included with the installer. However, you can choose to disable installation of certain components or use existing external instances of RabbitMQ or Flink. For more information, see Disabling Components.
When the installation is complete, the command line prompt is returned.
An advanced option is available if you want to override the default user account during the installation. For more information about launching the installer with this option, see Change the User Account. |
Disabling Components
To disable one or more of the Platform Analytics components during installation, add the following snippet to the installation launch command:
--disable-components <component_name>,<component_name>
The following table describes which code snippets to add or change to configure the installation:
Action | Code Snippet |
|---|---|
To prevent Descriptive Analytics Microservice from installing | Add the following to the launch command: --disable-components Descriptive_Services |
To prevent Property Transform Microservice from installing | Add the following to the launch command: --disable-components Property_Transform |
Enabling Anomaly Detection in a ThingWorx Cluster
To enable the use of Anomaly Detection, add the following snippet to the installation launch command:
If you enter true to enable TLS for the connection to Analytics Server, additional command parameters are required. For information about those parameters, see the table below. |
--enable-components analytics_server_integration ^
--ANALYTICS_SERVER_IP_ADDR "<IP address or host name>" ^
--ANALYTICS_SERVER_PORT <port where the Async microserver is running> ^
--ANALYTICS_SERVER_API_KEY <auto-generated API Key> ^
--ANALYTICS_SERVER_USE_TLS <true/false>
--ANALYTICS_SERVER_IP_ADDR "<IP address or host name>" ^
--ANALYTICS_SERVER_PORT <port where the Async microserver is running> ^
--ANALYTICS_SERVER_API_KEY <auto-generated API Key> ^
--ANALYTICS_SERVER_USE_TLS <true/false>
The table below describes the information required for each parameter in this snippet.
Launch Command Parameter | Description | ||||
|---|---|---|---|---|---|
--enable-components analytics_server_integration | Enables integration between your Analytics Server and Property Transform components. Analytics Server requires access to these components if you plan to deploy Anomaly Detection functionality in a ThingWorx cluster. | ||||
--ANALYTICS_SERVER_IP_ADDR | IP address or host name of your Analytics Server, which must already be installed and running. If you are using TLS for your connection to Analytics Server, this IP Address or Host Name must match the SAN address or host used to create the Analytics Server TLS certificate. | ||||
--ANALYTICS_SERVER_PORT | Port for communicating with your Async microservice. | ||||
--ANALYTICS_SERVER_API_KEY | Key generated automatically at the end of the Analytics Server installation. This key is required to interact with the Analytics Server internal API layer. If you did not make a note of the automatically-generated key, you must generate an updated key. See Updating an Analytics API Key. | ||||
--ANALYTICS_SERVER_USE_TLS
| Set to true if TLS authentication support is enabled for your Analytics Server microservices. The default is false.
| ||||
--ANALYTICS_SERVER_CERTIFICATE_FILE |
Path to the TLS certificate that was created for the Analytics Server installation. This is a JKS keystore file, however, for Platform Analytics, it must be converted to a PEM file. Use the following command to export the certificate from the keystore as a PEM file: keytool -exportcert -alias <analytics server alias> -keystore <keystore name>.jks -rfc -file <new file name>.pem
Enter the path to the new PEM file for the --ANALYTICS_SERVER_CERTIFICATE_FILE parameter. | ||||
--ANALYTICS_SERVER_TRUSTSTORE_PASSWORD |
Enter a password that will be assigned to the Analytics Server truststore. This truststore will be created automatically during the Platform Analytics installation. This is a new Analytics Server truststore, created by the Platform Analytics installer. |
This Analytics Server connection information is necessary only if you are planning to deploy Anomaly Detection functionality in a cluster of ThingWorx servers. If you are installing Platform Analytics for other reasons, you do not need to add these parameters to your launch command.
After Installation
When the installation is complete, the command line prompt will be returned.
To test the product installations, see:
• Verify the Descriptive Analytics Microservice Installation
• Verify the Property Transform Microserver Installation