Using SCIM with ThingWorx
System for Cross-Domain Identity Management (SCIM) is a standardized, automated method to keep user identities synchronized across disparate data stores and systems.
|
|
By default, SCIM is not started and is disabled upon platform start-up. Its enable and started states are controlled by the platform-settings.json configuration.
|
|
|
SCIM Endpoints for user/group management require credentials with Administrator rights. SCIM Endpoints are only accessible when configured to be enabled and when SSO is enabled.
|
For more information, see https://scim.cloud/.
ThingWorx supports the following:
• SCIM 1.1 – when PingFederate is the CAS
• SCIM 2.0 – when Microsoft Entra ID is the CAS and the IdP
• Outbound provisioning
• Create, update, and delete users or groups
• Configure defaults for SCIM-provisioned users and groups
For example, consider the following scenario:
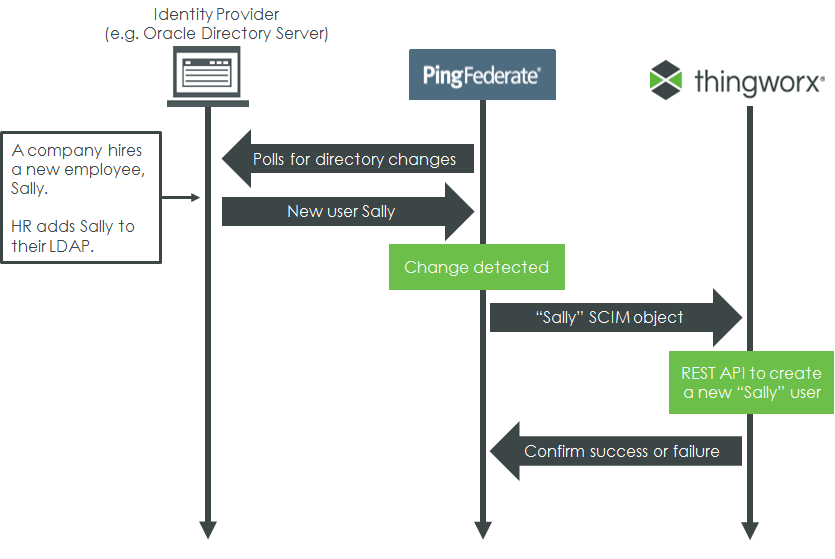
• The “Sally” SCIM object can contain any number of useful attributes (user name, email, phone number, etc.)
• If something changes (for example, Sally is promoted), SCIM can automatically update her ThingWorx user attributes accordingly. When Sally leaves the company, her ThingWorx user account is deleted or disabled when she is removed from the directory server.
Some user and group attributes may need additional configuration. This can be done when managing outbound provisioning from PingFederate. For more information, see the Ping Identity Knowledge Center: Specify custom SCIM attributes. The metadata mapping between ThingWorx User Extension properties and SCIM Schema 1.1 is fixed. For more information, see Create a Channel to the Data Store. |
Authentication
When SSO is enabled, ThingWorx requires OAuth tokens when provisioning through SCIM.
See the Ping Identity Knowledge Center for more information: Enable outbound provisioning |
When Microsoft Entra ID is the CAS and the IdP, the OAuth token type is JWT. |