Create a Channel to the Data Store
The following steps are performed from the PingFederate Administrative Console when configuring the outbound provisioning for your SCIM SP connection.
|
|
For more information, see the Ping Identity Knowledge Center: Managing channels.
|
1. Enter the following under Channel Info:
|
Channel Name
|
Enter a unique channel name.
|
|
Max Threads
|
1
|
|
Timeout (secs)
|
60
|
3. Under Source Settings, enter the following:
|
|
The following settings illustrate a connection to an Oracle Directory Server LDAP.
If you are using a different LDAP (such as Microsoft Active Directory), you will need to enter different values depending on your site. For more information, see the Ping Identity Knowledge Center: Modifying source settings.
|
|
Entry GUID Attribute
|
nsuniqueid
|
|
GUID Type
|
Text
|
|
Group Member Attribute
|
uniqueMember
|
|
User Object Class
|
person
|
|
Group Object Class
|
groupOfUniqueNames
|
|
Changed User/Groups Algorithm
|
Timestamp No Negation
|
|
Timestamp Attribute
|
modifyTimestamp
|
|
Account Status Attribute
|
nsaccountlock
|
|
Account Status Algorithm
|
Flag
|
|
Default Status
|
true
|
|
Flag Comparison Value
|
true
|
|
Flag Comparison Status
|
false
|
4. Under Source Location, enter the following:
|
Base DN
|
Enter the base DN where user records are stored in your LDAP. For example:
ou=twx_people,o=example
|
|
Filter (Users)
|
Construct a filter using the USER OBJECT CLASS value. For example:
(&(uid=*)(objectClass=person))
|
|
Filter (Groups)
|
Construct a filter using the GROUP OBJECT CLASS value. For example:
(&(cn=*)(objectClass=groupOfUniqueNames))
|
5. Under Attribute Mapping, review the default mapping.
|
|
These attributes will be different depending on your LDAP and data store. Refer to your user class schema and the following topics in the Ping Identity Knowledge Center: Configure attribute mapping and Specifying mapping details.
|
6. Ensure that each of the user attributes stored in the IdP, that you want to provision to ThingWorx, is listed in PingFederate to be provisioned. To list the user attributes in PingFederate, select Identity Provider and navigate to > > > .
|
|
The Type values for the fields in PingFederate are significant and must be configured correctly. For example, to ensure that office addresses are provisioned to ThingWorx, click Edit next to the Address Type field and select the Work value. See the image below. 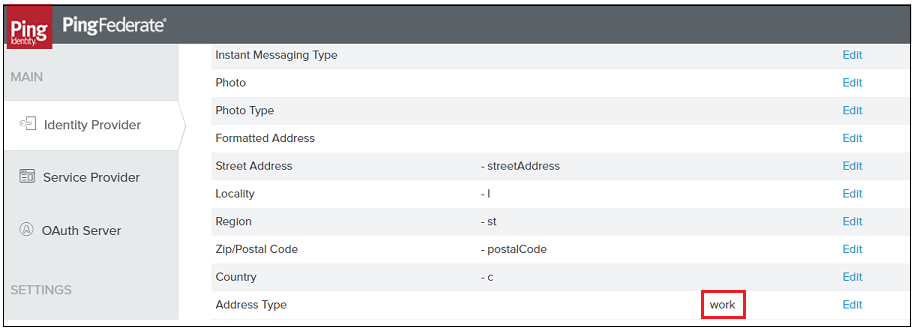 |
ThingWorx to SCIM 1.1/2.0 Mappings
Many provisioned attributes are mapped to ThingWorx User Extension collections. ThingWorx User Extensions can be customized. If you remove some of the attributes from the UserExtensions data shape, the corresponding attributes stored in the provisioner data store will not be provisioned to ThingWorx.
The following mappings are fixed. For more information, see Using Both SCIM and SAML Provisioning in the topic, Provisioning.
|
ThingWorx User and User Extensions
|
SCIM Schema 1.1/2.0
|
|---|---|
|
userName
|
userName
|
|
scimID
|
id
|
|
scimExternalId
|
externalId
|
|
firstName
|
givenName
|
|
middleName
|
middleName
|
|
lastName
|
familyName
|
|
fullName
|
displayName
|
|
title
|
title
|
|
emailAddress
|
emails::value(type=“work”)
|
|
altEmailAddresses
|
emails::value(type=“home”)
|
|
smsAddress
|
ims::value(type=“work”)
|
|
workPhone
|
phoneNumbers::value(type=“work”)
|
|
homePhone
|
phoneNumbers::value(type=“home”)
|
|
city
|
city
|
|
zipCode
|
postalCode
|
|
state
|
region
|
|
country
|
country
|
|
streetAddress
|
streetAddress
|