Managing Modeler and Web Interface Security
Microsoft SQL Server
Microsoft SQL Server is the Modeler database engine. The server runs as a windows service named sqlservr.exe on port 1433.
For information on how to change the default port number, refer to the following Microsoft SQL Server help topic:
Configure a Server to Listen on a Specific TCP Port
You should also ensure that the relevant ports are opened and secured.
For more information, see Setting up the Windows Firewall.
Network Shares
The following network share is created:
• ModelerATF – contains information on the models that are needed to locate the model when communicating with the Microsoft SQL Server service.
Those shares are used by the Modeler application to get the appropriate information on how to locate Microsoft SQL Server, databases, and models.
|
|
The contents of the database (models) is not exposed in those folders.
|
Shares use the standard Microsoft SMB network shares that operate on port 445. By default, those folders are publicly shared, but the visibility can be restricted by modifying the sharing configuration through the Windows sharing properties.
The following sharing properties are required:
• ModelerATF – all Modeler users should have Write permissions for the share property, associated folder, subfolders, and files.
|
|
By default, Everyone is granted Full Control to the share folder. You should restrict this so that only PTC Modeler users have access, and only Administrators have Full Control.
|
Access Rights Management
You can define access rights at database level to define database administrators. Administrators are users that are allowed to perform administrator functions on the Database. For example: Start, Stop, Backup, and Restore.
Using Model Explorer, you can define user access rights at the following levels:
• Database — sets database access permissions for users and groups for a specific database. For example: Read, Write, and Owner.
• Model — sets model access permissions for users and groups for a specific model. For example: Read, Write, and Owner.
• Package — sets package access permissions for users and groups for a specific package. For Example: Write and Owner.
If a user has read access to a model, they can see the contents of the entire model. However, they cannot modify the items without Write permissions for the relevant package.
For more information, see Controlling Access Using Package Protection and Access Rights.
Modeler Client, Automation Interface and Simulation
The Modeler client interacts with the database through TCP/IP and the user is authenticated using a Trusted Connection (usually the user’s Windows credentials).
The Automation Interface enforces the access rights rules that are defined on databases, models, and packages. For example, if a user does not have read access to a model, they will not be able to access the model information through the Automation Interface.
The Modeler UI uses port 15777 to receive instrumentation from simulation code generated from a model. The sender and receiver are typically on the same machine so access is not required from anywhere else on the network.
FlexLM Server (license)
The license mechanism relies on FlexLM. The following programs or ports need to be set up as firewall exceptions. In each case, the path shown is for a Modeler installation to the default locations. For more information, see Setting up the Windows Firewall.
• <<INSTALLDIR>>\License Manager\lmgrd.exe (for Floating License Server)
• <<INSTALLDIR>>\License Manager\artsansw.exe (for Floating License Server)
You should also ensure that the relevant ports are open and secure. For more information on ports and setting up the firewall, see Setting up the Windows Firewall.
PTC Modeler Web Interface
PTC Modeler Web Interface allows you to view the content of a model through a web browser. By default, PTC Modeler Web Interface is installed using HTTPS and requires a security certificate to be configured.
The Web Interface is an optional feature.
|
|
When you grant a user access to a Web Interface website, they can view all models that are set to Public Read or Public Write in all databases that can be accessed through the website.
|
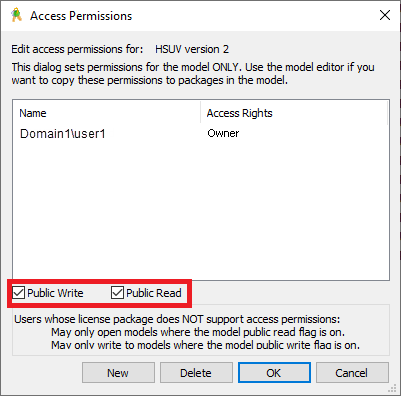
When you choose to install Web Interface, the Modeler installation program creates a Windows user account named PTC-IM-WSU, with a default password. You can change the password during the installation process, or after installation has completed. The Web Interface website uses the PTC-IM-WSU user account to access models.
To ensure security, we recommend changing the PTC-IM-WSU user account password. |
You can set up how users are authenticated when they log in to a Web Interface website. You can use:
• LDAP authentication,
• Web Interface website account authentication (local accounts created through the Web Interface administration),
• Both LDAP and Web Interface website account authentication
When using LDAP authentication, a user can view the following models through the Web Interface website: models that are Public Read or Public Write; and models for which the user has Modeler Owner, Write or Read access permissions.
The installation program sets up the Web Interface and Model Manager websites as HTTPS. You can configure HTTP for the websites if required. For information on configuring Websites as HTTP, see Configuring the Web Interface website to use HTTP.
Firewall rules must be added to allow access to the Modeler sites which are configured by default.
For more information, see Setting up the Windows Firewall.