Example: Windchill SSO Implementation with PingFederate as Broker
This example provides detailed steps on how to configure an environment that has Windchill PDMLink and Shibboleth SP configured for single sign-on with PingFederate as the Central Auth Server (CAS) and Active Directory Federation Services (ADFS) as the Identity Provider (IdP).
The following table displays the applications configured and their role in this example:
|
Role
|
Application
|
|---|---|
|
Service Provider
|
Windchill PDMLink + Shibboleth SP
|
|
Central Auth Server
|
PingFederate
|
|
Identity Provider
|
ADFS
|
|
Resource Server
|
Windchill
|
The following diagram displays the configuration discussed in this example.
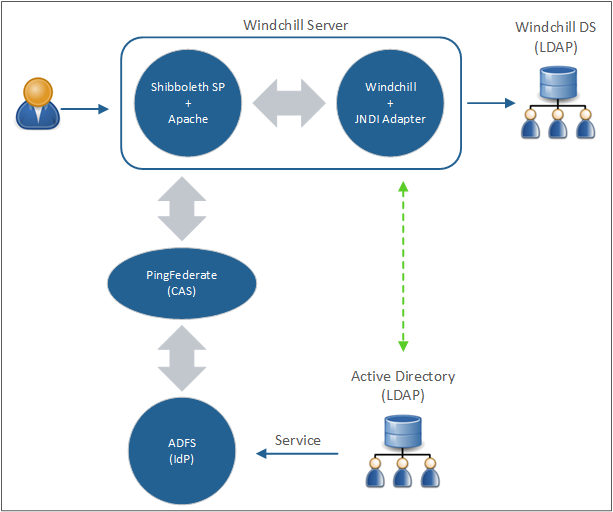
Part A: Prerequisites
1. Ensure that Windchill is set up. For more information, see the appropriate Windchill Help Center.
2. Setup and configure ADFS and ensure that you have included the following attribute values and files:
◦ uid
◦ email
◦ group
◦ Metadata file
Part E: Set up Shibboleth SP and PingFederate
To enable SAML capabilities for Windchill using Shibboleth Service Provider 2.6.0, complete the procedure in the following section of the Windchill Help Center: Security Assertion Markup Language (SAML) Authentication. Follow the instructions in these sections of the same Windchill Help Center page:
• Troubleshooting and Debugging the Shibboleth Service Provider
• Restarting the Shibboleth Service Provider and PTC HTTP Servers
Part F: Set up a JNDI LDAP Entry
To configure a JNDI adapter, complete the procedure in the following section of the Windchill Help Center: JNDI Adapter LDAP Entry.
Part G: Additional Configuration
If your Windchill workflow requires the use of eSignature, some additional configuration is necessary to deploy SSO. For more information, see the following sections of the Windchill Help Center:
For additional considerations, see the Client Compatibility section of the Windchill Help Center: