Configure the SSL Certificate for Application Layer Encryption and Signing
Configure SSL certificates for applications, such as ThingWorx and PingFederate, for the following purpose:
• SAML signing and signature verification—Establishes trust and verifies the original source of the request.
• XML encryption and decryption—Provides secure communication of SAML response.
SAML Signing and Signature Verification
The signing is done by a private key and the signature verification is done by a public key.
In the signing and signature verification process:
◦ Any communication from the service provider to CAS is signed by the service provider private certificate. On the CAS, the signature verification is done by the service provider public certificate. Further, the communication is signed again on the CAS by the CAS private certificate and on the identity provider (IdP), the signature verification is done by the CAS public certificate.
◦ Any communication from the IdP to CAS, is signed by the IdP private certificate. On the CAS, the signature verification is done by IdP public certificate. Further, the communication is signed again on the CAS by the CAS private certificate and on the service provider, the signature verification is done by the CAS public certificate.
The following figure shows the signing and signature verification process between various applications.
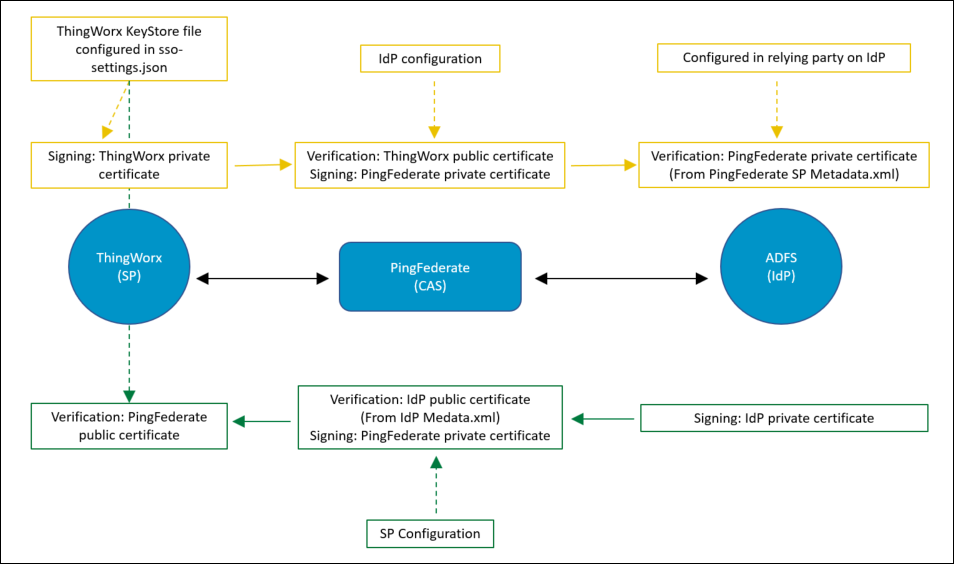
In the figure:
◦ ThingWorx is the service provider, PingFederate is the CAS.
◦ The ThingWorx private certificate and PingFederate public certificate are configured in the KeyStore file referenced by the ThingWorx SSO configuration.
◦ The ThingWorx public certificate and PingFederate private certificate are configured in the IdP configuration section on the PingFederate server.
◦ The IdP public certificate and PingFederate private certificate are configured in the service provider configuration section on the PingFederate server. The IdP public certificate is included in the IdP Metadata.xml file.
◦ The PingFederate public certificate is configured in the relying party configuration on IdP. This certificate is included in the Metadata.xml file of the service provider, which is exported from the PingFederate server.
XML Encryption and Decryption
SAML responses, which also contain the assertion, from IdP to CAS and CAS to service provider are encrypted and decrypted. Same certificates are used for signing and encryption.
Any communication from the IdP to CAS, is encrypted by the CAS public certificate and on the CAS, the communication is decrypted by the CAS private certificate. Further, the communication is encrypted again on CAS by the service provider public certificate. On the service provider, the communication is decrypted by the service provider private certificate.
The following figure shows the XML encryption and decryption.
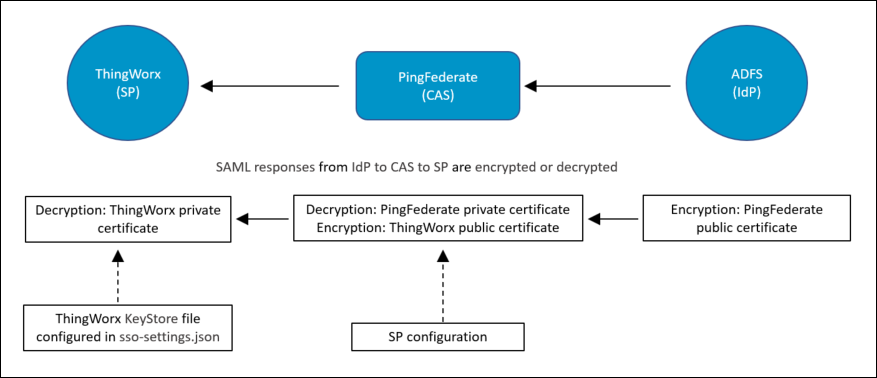
In the figure:
◦ ThingWorx is the service provider, PingFederate is the CAS.
◦ The ThingWorx private certificate is configured in a KeyStore file on the ThingWorx server that is referred in the sso-settings.json file.
◦ The ThingWorx public certificate and PingFederate private certificate are configured in the service provider configuration section on the PingFederate server.