Setting Up Security Access Control for Connected Field Service
The Connected Field Service application uses the ThingWorx security model for control of access rights for users and connected devices. The following sections provide information on the setup of access control for Connected Field Service.
For more information on the ThingWorx security model, refer to the ThingWorx documentation available from the
Help Center page at
http://support.ptc.com.
Using Limited Access Accounts for Connected Devices
The devices connected to the ThingWorx platform must be configured with all access rights required for the interaction with the Remote Access application. It is not required, but strongly suggested, that you use non-Administrator accounts for your connected devices.
Creating Application Keys for Connected Devices
Typically, connected devices are authenticated using a ThingWorx Application Key.
1. Create one or more ThingWorx Application Keys (appkeys) for the connected devices. Map keys to devices as appropriate for the installation:
◦ One for all devices
◦ One for each device
◦ One for some subset of devices
2. Map the appkeys to one or more Thingworx users as appropriate for the installation.
3. Add the appropriate ThingWorx users to the PTC.CSLM.Devices user group.
This could be a single appkey and user for all devices or one appkey/user pair per device or any combination in between. The key point is to ensure that all users associated with appkeys for any connected devices are assigned to the PTC.CSLM.Devices User Group. This will allow the devices to have a consistent and manageable set of access rights for any needed CSLM capabilities such as Connected Field Service.
Enabling Application Keys in HTTP requests
If you are running Thingworx 8.1 or later, follow the steps below to set the Allow Application Key as URL Parameter option. This setting will allow an Application Key to be used when accessing Thingworx from ServiceMax so that the user is not challenged for credentials.
1. Select System from the menu on the left side of the screen.
2. Under System, select Subsystem.
3. Click PlatformSubsystem.
4. Click Configuration.
5. Select Allow Application Key as URL Parameter
6. Click Save.
Creating a User Group for Restricted Use of the ThingWorx Workflow Manager
The connected devices initiate services in the ThingWorx Workflow Manager.
|
|
These steps are for ThingWorx Utilities 7.1. Later releases of ThingWorx Utilities include a BP User Group for execution of business processes.
|
To allow the PTC.CSLM.Devices User group to execute ThingWorx Utilities Business Processes, do the following:
• In Thingworx, create a new user group. A suggested name to use is “BusinessProcessExecutors.”
• Add the PTC.CSLM.Devices as a member of the BusinessProcessExecutors User Group.
Granting the Needed Access Rights for the ThingWorx Workflow Manager
Pay close attention to the very similar names of the two templates that need to be configured:
|
|
These steps are for ThingWorx Utilities 7.1 and may change in later releases.
|
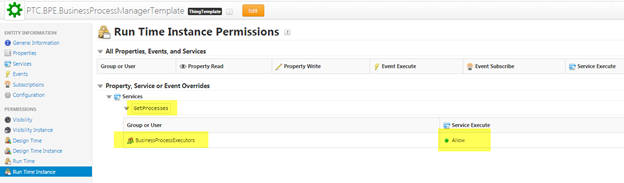
• In Thingworx edit the access control for PTC.BPE.BusinessProcessManagerTemplate, specifically, the Run Time Instance rights. Add the following right:
GetProcesses | BusinessProcessExecutors | Service Execute
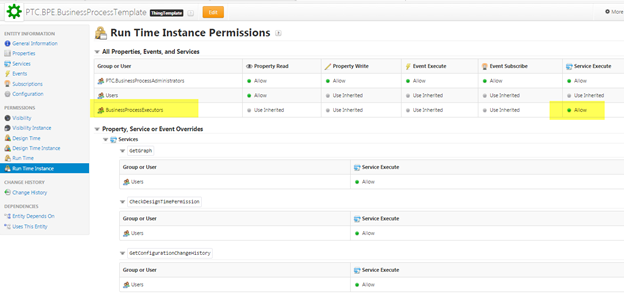
• Do the same for PTC.BPE.BusinessProcessTemplate:
All Properties, Events and Services | BusinessProcessExecutors | Service Execute
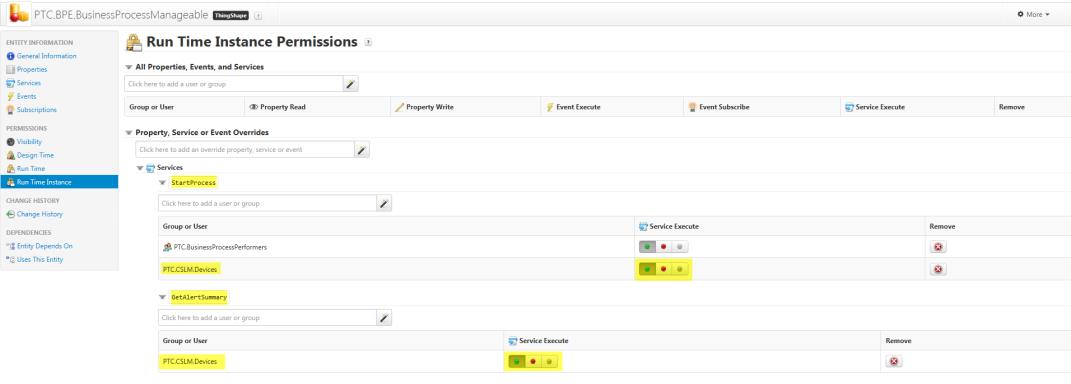
Other Access Control issues for Entities
If you are using your own Entity hierarchy with the Business Process Engine or your own backing services, be aware that Entities implementing the ThingShape PTC.BPE.BusinessProcessManageable must allow access to the following services: StartProcess, GetAlertSummary