Reverse Proxies
PTC web-based products support users logging in to sites from within and outside the firewall. With users logging in to PTC products from outside the firewall, PTC can help you minimize the risk to your infrastructure from intruders. One way to allow outside enterprise resources access to the enterprise web-based applications supplied by PTC is by using a reverse proxy configuration.
The following sections explain the basics of how to architect and configure various solutions but also how to configure them. Not all of the possible configurations are documented. Use the sections to educate yourself, and then apply what you have learned to your situation.
Background
A reverse proxy is a special deployment case of a proxy server. In a reverse proxy, the reverse proxy server can be located in the following locations:
• Outside of the firewall
• Inside a firewall
• Within a demilitarized zone (DMZ), an area between two firewalls, that represents a content server to external clients
A reverse proxy deployment allows you to expose specific content provided by a web server without actually exposing the web server to the client.
In a reverse proxy, the proxy server functions like a web server with respect to the clients it services. Unlike internal clients, external clients are not reconfigured to access the proxy server. Instead, the site URL routes the client to the proxy as if it were a web server. Replicated content is delivered from the proxy cache to the external client without exposing the original server or the private network residing safely behind the firewall.
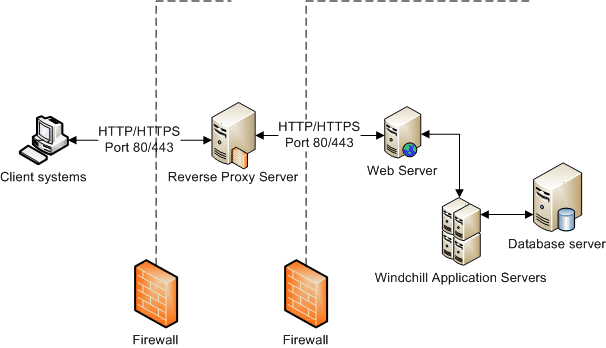
The following diagram displays some of the basic components of a reverse proxy configuration. In this diagram, the proxy server is between two firewalls:
This type of configuration is a basic configuration. The area between the two firewalls is known as a demilitarized zone (DMZ). If someone takes control of the proxy server, the person does not have control of the application server nor does the person know the location of the application server. Notice the firewall between the client systems and the proxy server, and between the proxy server and the web server. This second firewall makes this is a very secure environment.
Basic Reverse Proxy Configuration
Setting up your environment to use a reverse proxy server involves the use of two host machines:
• On one host, set up a web server to use as the proxy web server. For example, install HTTP Server on the server1 host named server1.mycompany.com.
• On the second host, set up Windchill. For example, install Windchill on the server2 host named server2.mycompany.com.
There are unique tasks to complete on each host:
• On the Windchill server host (server2), update the following:
◦ wt.properties as directed in the section Updating wt.properties on the Windchill Host.
◦ web.xml as directed in the section Updating web.xml on the Windchill Host.
• On the proxy server host (server1), update the proxy web server httpd.conf file as directed in the section Updating wt.properties on the Windchill Host.
Additionally, you can set up the reverse proxy server for secure access using HTTPS as described in the section Using HTTPS with a Reverse Proxy Server.
Updating wt.properties on the Windchill Host
| When updating the wt.properties file, use the xconfmanager utility from within a Windchill shell. For information on using this utility, see About the xconfmanager Utility. |
The Windchill host name should resolve to the reverse proxy server for clients that are required to access through the reverse proxy. To generate outgoing Windchill URLs referencing the reverse proxy server, you must set the following properties in the wt.properties file. These properties map the Windchill server codebase to the reverse proxy codebase:
wt.server.codebase=http://<proxy_server_host_name>[:<port>]/<web_app_name>
wt.httpgw.mapCodebase=http://<Windchill_host_name>[:<port>]/<web_app_name>
Reverse Proxy wt.properties Example
Assume the following statements are true:
• The fully qualified reverse proxy host name is server1.mycompany.com.
• The fully qualified Windchill host name is server2.mycompany.com.
• The web servers on both hosts use the default port.
• The value in the wt.adapter.simpleTaskDispatcher.minPort property (<task_dispatcher_minPort>) is the default value of 18080.
• The web application name (<web_app_name>) defined when Windchill was installed on the Windchill server host is Windchill.
Then, the wt.properties properties to set using the xconfmanager utility are as follows:
wt.rmi.clientSocketFactory=wt.boot.WTRMIMasterSocketFactory
wt.rmi.javarmicgi=servlet/JavaRMIServlet
wt.server.codebase=http://server1.mycompany.com/Windchill
wt.httpgw.mapCodebase=http://server2.mycompany.com/Windchill
Updating web.xml on the Windchill Host
The ports set in the servlet declaration for the JavaRMIServlet in the web.xml file (located in the WEB_INF subdirectory of the codebase directory) are automatically handled by using a port range. The usage of the range starts with the lowest of the values and continues to the highest of the values. The values are stored in the following properties that are in the wt properties file:
• wt.manager.port
• wt.method.minPort
• wt.method.maxPort
To change the range, set the properties using the xconfmanager utility.
The defaults for minPort and maxPort are 5002 and 5011:
<servlet>
<servlet-name>JavaRMIServlet</servlet-name>
<description>RMI over HTTP proxy</description>
<servlet-class>wt.tools.javarmi.JavaRMIServlet</servlet-class>
<init-param>
<param-name>minPort</param-name>
<param-value>5002</param-value>
</init-param>
<init-param>
<param-name>maxPort</param-name>
<param-value>5011</param-value>
</init-param>
</servlet>
<servlet-mapping>
<servlet-name>JavaRMIServlet</servlet-name>
<url-pattern>/servlet/JavaRMIServlet/*</url-pattern>
</servlet-mapping>
Configuring an Apache-based Web Server as a Reverse Proxy Server
This section is intended to provide a reverse proxy example that has minimal details on configuring an Apache httpd server. PTC does not endorse or support any particular reverse proxy product. Each reverse proxy implementation has its own requirements that need to be evaluated by system and network administrators.
Remove the comment characters from the following lines in the httpd.conf file:
LoadModule proxy_module modules/mod_proxy.so
LoadModule proxy_connect_module modules/mod_proxy_connect.so
LoadModule proxy_http_module modules/mod_proxy_http.so
Add following lines at the end of the httpd.conf file (some lines have been split to fit the width of the page):
ProxyPass /<web_app_name>/ http://<Windchill_host_name>/
<web_app_name>/ProxyPassReverse /
<web_app_name>/ http://<Windchill_host_name>/<web_app_name>/
/* To access Solr URL on Reverse Proxy Server */
ProxyPass /<web_app_name>-Solr/ http://<Windchill_host_name>[:<port>]/
<web_app_name>-Solr/
ProxyPassReverse /<web_app_name>-Solr/
http://<Windchill_host_name>[:<port>]/<web_app_name>-Solr/
Where the values for <web_app_name> and <Windchill_host_name> are the same values you entered in the section Updating wt.properties on the Windchill Host.
Using HTTPS with a Reverse Proxy Server
Typical use of a reverse proxy server requires all incoming traffic to be HTTPS. An HTTPS reverse proxy server may be used to proxy to an HTTP web server for
Windchill using the same configuration steps as documented previously. However, any reference to the reverse proxy server URL needs to reference the HTTPS protocol and proper port instead of the HTTP protocol. If external users are required to use HTTPS while internal users are allowed to use HTTP, then dual
Windchill servers should be used, one configured with HTTPS URLs and the other with HTTP URLs. For more information about HTTPS URLs and HTTP URLs, see
Dual HTTP and HTTPS Protocol Systems.