Replication with Security Labels
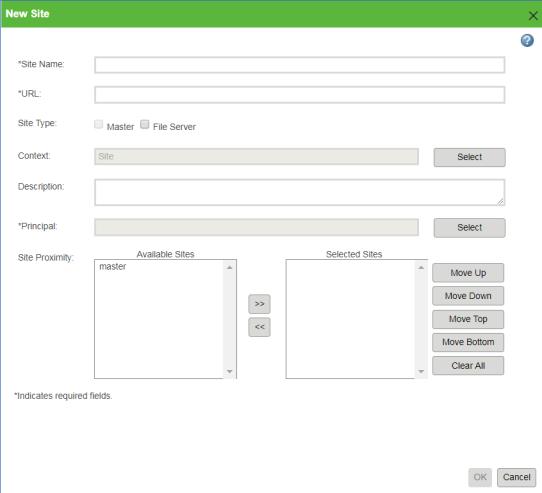
When a new replica site is created, a principal (user or group) is selected to be the site principal, by clicking Select next to the Principal field:
This principal is used as the session principal for a replication session for that replica site. For objects to be replicated to the replica site, the principal specified for that site must have access to that object. When security labels are enabled, this means that for an object to be replicated to the replica site, the user or group specified as the site principal must be an authorized participant for all security label values on that object.
The following types of replication are impacted:
• Scheduled replication – Only objects to which the site principal has access are replicated.
• User initiated replication – When replication is initiated, only objects to which the site principal for chosen replica site has access are replicated, even if the user initiating the replication has access to the objects.
• Ad-hoc replication – The object is only added to the user's preferred replica site if the site principal for that site has access to the object. If the site principal does not have access to the object, the user is provided a direct download URL from the proximity site.
• Predictive replication – If the site principal does not have access to the object, a predictive cache rule is not created. If a predictive cache rule already exists for the object, but the site principal does not have access to it (either the site principal has been changed, or the access rights on the object have changed so that the site principal no longer has access), the object is not replicated.
| Constraints imposed by security labels may cause a file upload to switch to a less proximal file server. Care should be taken during file server proximity specification, to ensure that all file uploads that are considered legitimate will ultimately find a file server in the proximity list which is acceptable to any security label that may be created. |
For more information on replication, see
Replication and
File Server Administration.