eSignature Validation for SSO Configurations
The following topic is relevant to the following users:
• You want to require users to provide credentials before submitting their electronic signature.
• Your site provides authentication through a single sign-on (SSO) configuration and Identity Provider (IdP).
Configure Apache
1. Add following text to <APACHE_HOME>/conf/conf.d/30-app-Windchill-1Auth.conf:
<LocationMatch ^/+Windchill/reauthsecure?>
AuthType shibboleth
ShibRequestSetting applicationId reauthsecure
ShibUseHeaders on # mod_jk doesn't pass environment, so useHeaders is required
require shib-session
</LocationMatch>
2. Navigate to <APACHE_HOME>/conf/conf.d/00-1mod_shib.conf.
Locate <Location /Shibboleth.sso>. Immediately after the closing tag, add the following:
<Location /reauthsecure/Shibboleth.sso>
AuthType None
require shib-session false
</Location>
3. Add the following text to the end of 00-1mod_shib.conf:
Alias /Windchill/reauthsecure/ "/reauthsecure/Shibboleth.sso/Login"
<Location /reauthsecure>
AuthType shibboleth
ShibRequestSetting applicationId reauthsecure
require shib-session
</Location>
4. Restart the Apache server.
Configure Shibboleth
Navigate to <SHIBBOLETH_INSTALL_DIRECTORY>/etc/shibboleth/shibboleth2.xml.
1. Add the following tag inside the <HOST> element. The target functionality behaves like a new application, and as a result the server forces the user to reauthenticate:
<Path name="reauthsecure" authType="shibboleth" requireSession="true" forceAuthn="true" applicationId="reauthsecure" />
For example:
<Host name="sp.example.org">
<Path name="secure" authType="shibboleth" requireSession="true"/>
<Path name="reauthsecure" authType="shibboleth" requireSession="true" forceAuthn="true" applicationId="reauthsecure" />
</Host>
2. Add the following tag inside the <ApplicationDefaults> element. This overrides the default application:
<ApplicationOverride id="reauthsecure" entityID="SP_CONNECTION_NAME" REMOTE_USER="uid eppn persistent-id targeted-id" cipherSuites="ECDHE+AESGCM:ECDHE:!aNULL:!eNULL:!LOW:!EXPORT:!RC4:!SHA:!SSLv2" >
<Sessions lifetime="1" timeout="1" checkAddress="false" relayState="ss:mem" handlerURL="/reauthsecure/Shibboleth.sso" maxTimeSinceAuthn="2" >
<SSO entityID="PTC-Capricorn-PingFederate" discoveryProtocol="SAMLDS" discoveryURL="https://ds.example.org/DS/WAYF" forceAuthn="true" >
SAML2 SAML1
</SSO>
<!-- SAML and local-only logout. -->
<Logout>SAML2 Local</Logout>
<!-- Extension service that generates "approximate" metadata based on SP configuration. -->
<Handler type="MetadataGenerator" Location="/Metadata" signing="false"/>
<!-- Status reporting service. -->
<Handler type="Status" Location="/Status" acl="127.0.0.1 ::1"/>
<!-- Session diagnostic service. -->
<Handler type="Session" Location="/Session" showAttributeValues="true"/>
<!-- JSON feed of discovery information. -->
<Handler type="DiscoveryFeed" Location="/DiscoFeed"/>
</Sessions>
</ApplicationOverride>
|
|
It is possible that network latency may cause the session timeout to expire prematurely. PTC recommends that you adjust timeout values as needed to ensure the action can be completed.
|
3. Restart the Shibboleth service.
Configure IdP
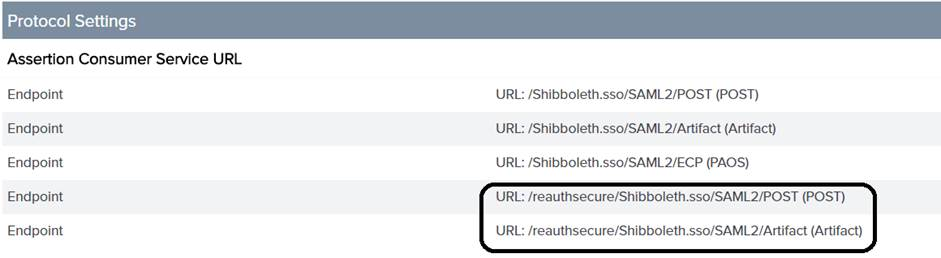
Configure your IdP to add the following endpoints to your existing Service Provider (SP) connection:
/reauthsecure/Shibboleth.sso/SAML2/POST
/reauthsecure/Shibboleth.sso/SAML2/Artifact
For example, if you use PingFederate, you would perform the following steps:
1. From the administrative console under > , click the SP name.
2. From the SP Connection page, select Browser SSO and click Configure Browser SSO.
3. From the Configure Browser SSO page, select Protocol Settings and click Configure Protocol Settings.
4. Under Assertion Consumer Service URL, add the following endpoints and save the configurations:
/reauthsecure/Shibboleth.sso/SAML2/POST
/reauthsecure/Shibboleth.sso/SAML2/Artifact
Update wt.properties
Update wt.properties to change the value of the wt.org.electronicIdentification.class property to wt.workflow.engine.SSOConfiguredSignatureEngine:
wt.org.electronicIdentification.class=wt.workflow.engine.SSOConfiguredSignatureEngine