Security Labels and Access Control
Security labels are applied in addition to standard Windchill access control policy and ad hoc rules. A security label acts as a gate; if the user is not cleared for the security labels on an object, they cannot access the object, even if their access control permissions would otherwise allow them access. If the user does not have the necessary access control permissions, they cannot access the object, even if they are cleared for the security label settings on the object. To access an object, a user must be cleared for all security labels, either as an authorized participant or by an active agreement, and have proper access control permissions for that object.
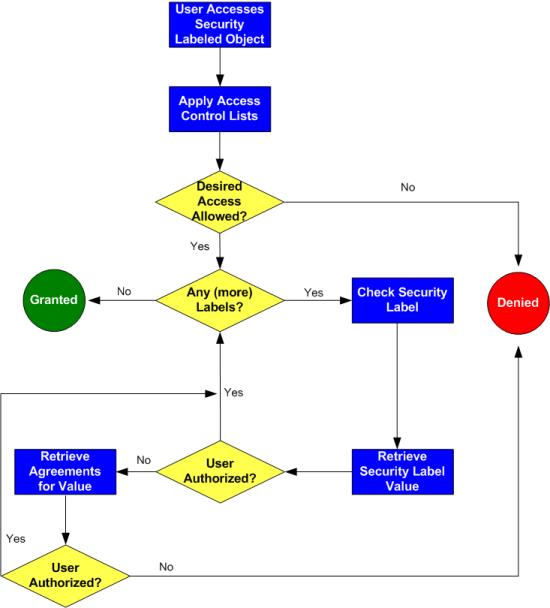
The following flow chart provides an overview of how Windchill processes security labels and access control to grant or deny a user access to an object.
When determining if a user can access an object, the system first checks policy and ad hoc access control lists to see if the user has the necessary access control permissions. If the desired access is allowed, then the system checks to see if the user is authorized for all security labels on the object, to determine if access is granted or denied.
If the user is not an authorized participant for a security label value, the system checks to see if the user is authorized for that value by one or more active agreements. If an appropriate agreement is in effect, and the user is authorized for the remaining security labels, access is granted. If no appropriate agreement is in effect, access is denied.