Encryption Customization for Amazon S3 Mounts
This section explains the encryption customization to store content in an encrypted format on Amazon S3. Out of the box, the content stored on Amazon S3 is encrypted using serverSideEncryption-s3 encryption type. The content stored in file based vaults are in plain format.
|
|
User is responsible for managing the encryption options. You should make sure that the content is accessible in case of changes in encryption options.
|
To customize the encryption of content on Amazon S3 write delegate implementations as follows:
1. S3 Encryption Configurator Delegate-Type the delegate to choose the encryption type. If you want to use other encryption type, you should write a delegate that returns the expected encryption type, deploy the class files at master site and at registered File Servers, that is replica sites, and configure using the command line tool. The default value of the delegate is
com.ptc.windchill.objectstorage.amazons3.encryption.DefaultS3EncryptConfigurator. The default delegate returns the encryption type as
serverSideEncryption-s3. If you want to use other encryption type, you need to write a delegate that returns the expected encryption type, deploy the class files and configure using this command line tool. If you want to use other encryption type, you need to write a delegate that returns the expected encryption type. For more details on configuration, see
Configuring Windchill File Vaults to use Amazon S3.
Following is a sample delegate.
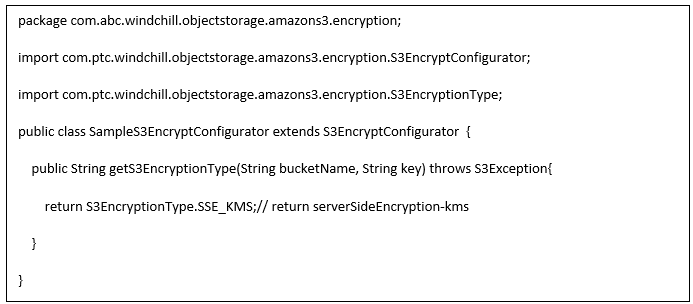
SampleS3EncryptConfigurator.java:
TheSampleS3EncryptConfigurator returns the serverSideEncryption-kms as the encryption type. The content stored on Amazon S3 gets encrypted using KMS encryption. The API getS3EncryptionType receives the bucket name and object key as argument. You can program the encryption type using the bucket name and object key. For example, for bucket b1, return encryption type as serverSideEncryption-kms, and for bucket b2, return the encryption type as serverSideEncryption-s3.
Valid values of encryption type are:
a. serverSideEncryption-s3 — The content is stored using server side encryption with AWS S3 managed keys.
b. serverSideEncryption-kms — The content is stored using server side encryption with AWS KMS managed keys.
c. serverSideEncryption-customerProvidedKeys — The content is stored using server side encryption with customer provided keys.
2. SSEKMSKeyProvider Delegate — Type the delegate to identify the KMS Key ID during encryption of content on Amazon S3. This delegate is applicable if encryption type is configured as
serverSideEncryption-kms. Windchill supplies default implementation of this delegate. The default implementation uses the default AWS KMS Key ID which is specific to a region. If you want to use other KMS Key IDs, you need to write the implementation for this delegate and configure this delegate to select your implementation. This delegate is applicable if the encryption type is configured as
serverSideEncryption-kms. The default out-of-the-box value of the delegate is
com.ptc.windchill.objectstorage.amazons3.encryption.ssekms.DefaultSSEKMSKeyProvider. If the default delegate returns the KMS Key ID as none, then the default AWS KMS Key ID is used for encryption. If you want to use your own KMS Key IDs, then you should write a delegate that returns the expected KMS Key IDs, deploy the class files and configure using this command line tool. For more details on configuration, see
Configuring Windchill File Vaults to use Amazon S3.
| Do not use this implementation as is in a production environment. |
Sample delegate is as follows:
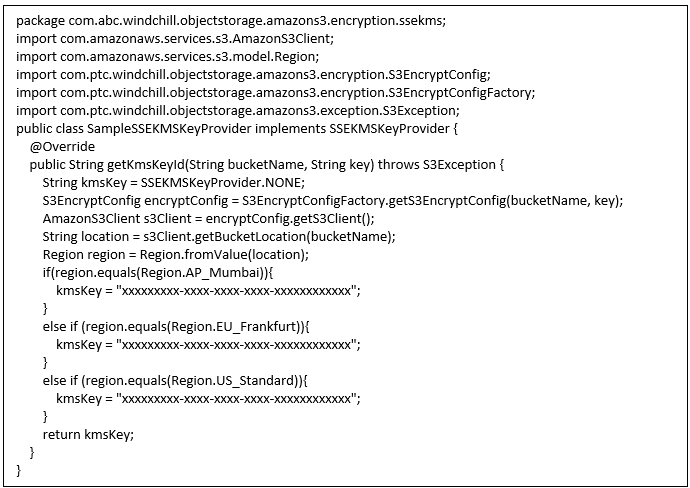
SampleSSEKMSKeyProvider.java:This sample implementation demonstrates how you can return the KMS Key ID for a specific region. Here we first get the AmazonS3Client object. Using AmamzonS3Client, we retrieve the location and region for a given bucket name. Check AWS java doc for more details on this.
3. SSECSecKeyGenerator Delegate — If you configure the encryption type as
serverSideEncryption-customerProvidedKeys, you should write the implementation for this delegate and configure the delegate. This delegate is applicable only if the encryption type is configured as
serverSideEncryption-customerProvidedKeys. There is no default out-of-the-box implementation for this delegate. Write a delegate that manages the Secret Keys, deploy the class files and configure using this command line tool. For more details on configuration, see
Configuring Windchill File Vaults to use Amazon S3.
Sample delegate is as follows:
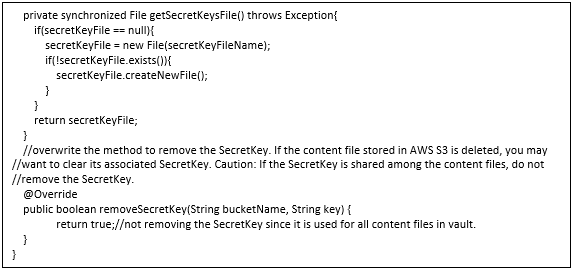
SampleSSECSecKeyGenerator.java: This is a sample implementation that demonstrates how to generate a SecretKey. This sample implementation searches for an existing SecretKey. If found the SecretKey is returned. Otherwise generate a new SecretKey, store it in a file on disk and return. You can decide the strategy to securely store the SecretKey. Also this sample implementation is using the single SecretKey for all the files in vault. You can write your own algorithm to manage the multiple SecretKeys for buckets or for objects stored in AWS S3

.
 .
.