Non-Null Label Values and Their Authorized Participants
A security label can have multiple non-null label values. For standard security labels, each non-null label value can be associated with a participant who is unrestricted by the security label value. Only one authorized participant can be assigned to each security label value. For both standard and custom security labels, there are multiple ways to specify the authorized participants:
• Using a Unique Federation Identifier (UFID), which limits the authorized participants to only the participant identified in the UFID (if the participant is a user) or to the participant and its members (if the participant is a user-defined group or organization).
• Using WTPrincipalReference, if group is created in database and not in LDAP. For more details see Specifying a WTPrincipalReference.
• Using a custom evaluator class, which allows you to customize how to determine if a user is an authorized participant.
• Using a combination of the UFID and a custom evaluator class.
For more information about the custom evaluator class, the differences between the type of authorized participants, or about setting up custom security labels, see the “Customizing Security Labels” topic in the Advanced Customization section.
Specifying a user-defined group as the authorized participant provides the most flexibility, as membership in the group can be modified as needed using the Participant Administration utility, the > page, or a third party LDAP tool to manage groups within an LDAP directory service. If a group is used as the authorized participant for a security label value, the membership of the group can include other groups. While there is no explicit hierarchy among security label values, a hierarchy can be achieved by nesting groups within other groups.
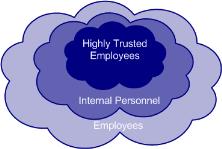
For example, the Corporate Proprietary standard security label is created with three values: Private, Internal, and Company Most Private. Three authorized participant groups are available for the Corporate Proprietary security label, each with clearance to one security label value:
• The Employees group is cleared for the Private security label value.
• The Internal Personnel group is cleared for the Internal security label value and is a member of the Employees group and therefore is cleared for the Private security label value.
• The Highly Trusted Employees group is cleared for the Company Most Private security label value and is part of the Internal Personnel group and therefore cleared for the Private and Internal security label values as well.
Each standard security label value or custom security label can also optionally have an associated agreement type. Users who are not authorized participants for that standard security label value or any value of the custom security label are denied access to objects with that label value applied, unless they are specifically granted temporary clearance to the object by membership in an authorized participants list for an active agreement.
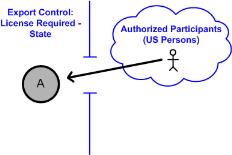
For example, a site could configure an Export Control standard security label, with values of No License Required, License Required - State, and Do Not Export.
• No License Required is the null value and does not restrict any user from accessing objects with this security label value.
• License Required - State allows access to only members of the US Persons group.
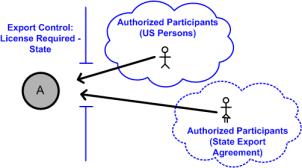
If the License Required - State value has an associated agreement type of State Export Agreement, the users who are not in the US Persons group, but meet the necessary licensing requirements can be granted temporary clearance to objects marked with the License Required - State value through use of an active State Export Agreement. When the agreement is created, users who are not members of the US Persons group can be added to the authorized participants list of the agreement to be temporarily cleared for the License Required - State value on any associated objects.
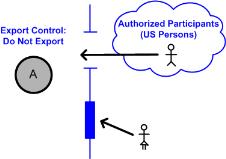
• Do Not Export restricts access to only members of the US Persons group. There is no associated agreement type for this value, so there is no way to grant temporary clearance to users who are not in the US Persons group.
If the site also has a Corporate Proprietary security label configured, with its own set of label values and authorized participants, a user must be authorized for both security labels to access the object. For example, if a user is only a member of the US Persons group, which is the authorized participant group for the License Required - State label value, he will not be able to access an object that also has the Internal label value applied. Likewise, a user who is only a member of the Internal Personnel group, the authorized participant group for the Internal label value, will not be able to access the object that also has the License Required - State value applied. Only a user who is cleared for all label values, through membership in all authorized participant groups or through an agreement, will be able to access the object.
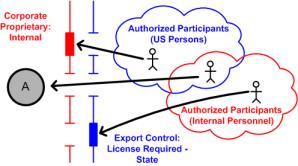
Being authorized for one security label does not automatically authorize a user for any other security label. Users must be cleared for all security labels that are set on an object to be able to access the object.