Configuration Required to Access Data from Windchill+
This section describes the configuration required to access data from the Windchill+ environment. This configuration is required to retrieve your data exported using Windchill+ integrations such as ERP Connector to a Windchill+ Azure storage account. You can then transfer this data to your own service or consume it for integration. For more information, see Support for Outbound Data Flow.
The shared storage of Windchill+ is configured with firewall rules for security and safety of the shared data.
Prerequisite
To access this storage, the firewall configuration must identify the IP/CIDR or Azure Virtual Network (VNet) subnet Service Endpoint from which it is being accessed. Therefore, the egress IP/CIDR of the system or service accessing this storage is necessary. When such a service is hosted on public cloud vendors like Microsoft Azure, Amazon Web Service (AWS), Google Cloud Platform (GCP), a private cloud, on-premises infrastructure, or a private IP, the CIDR block information is required for firewall configuration.
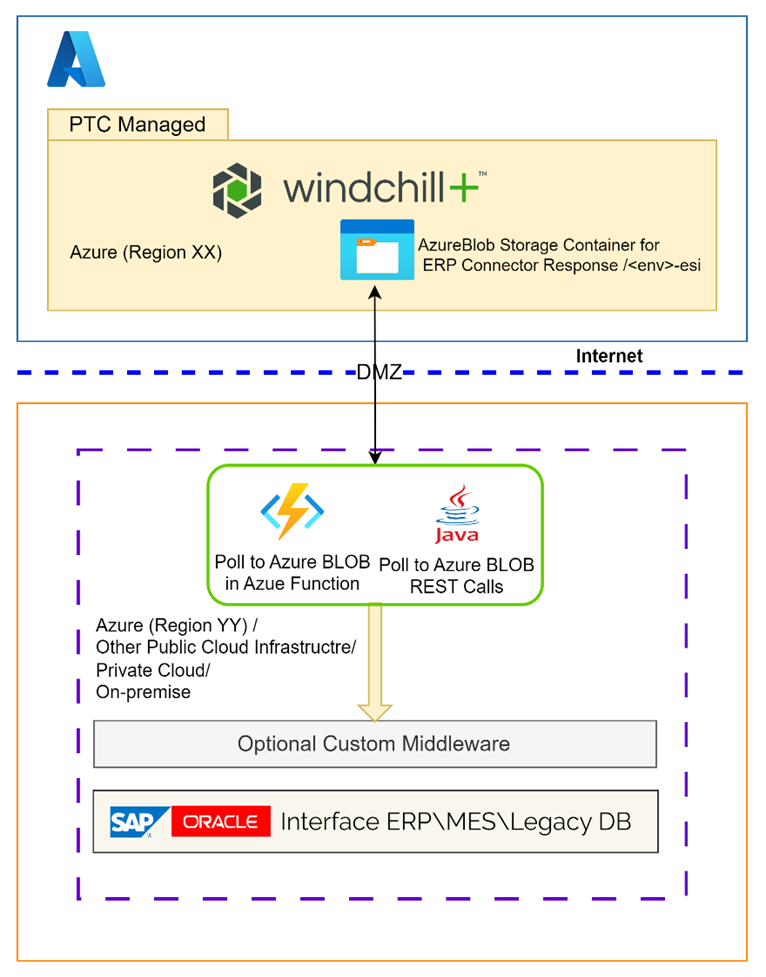
If your Azure service or integration is running in an Azure cloud region, and the Windchill+ service is also running in the same region as per your choice, then the storage firewall requires a Service Endpoint ID.
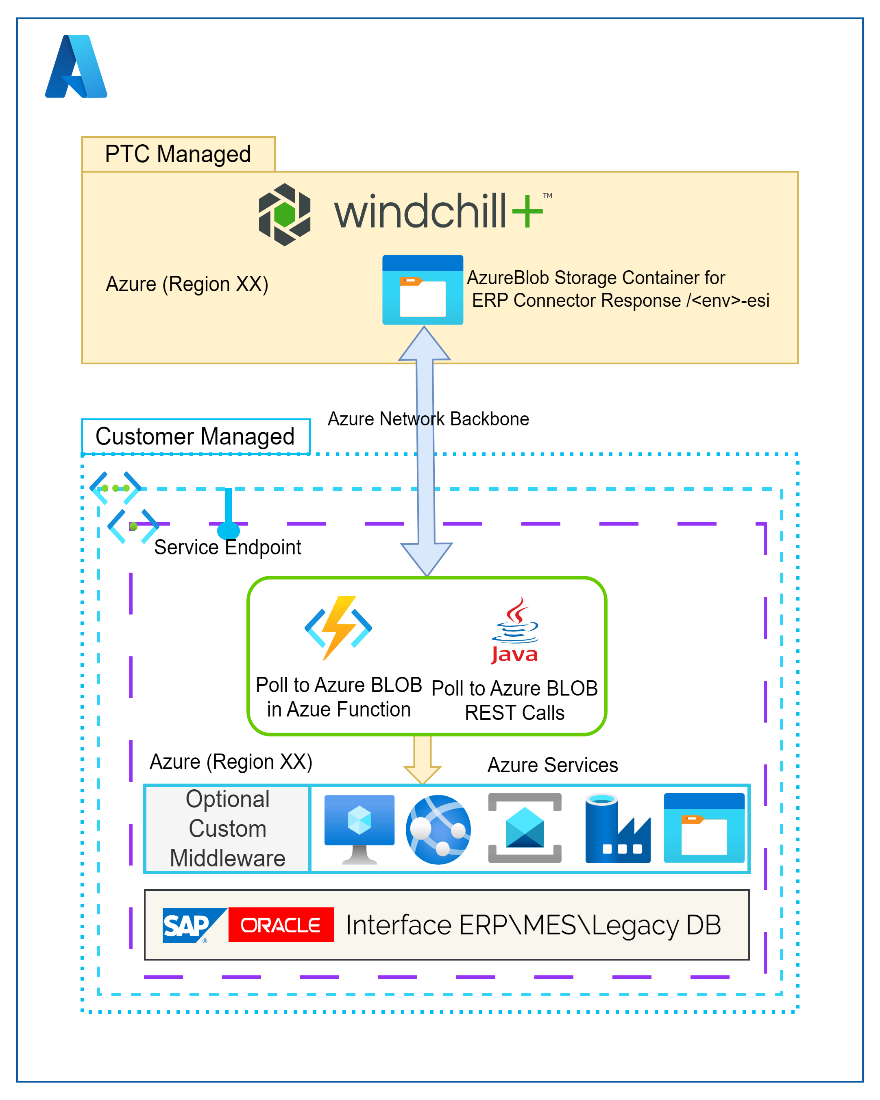
Overview
Establish a Service Endpoint to allow PTC customer managed services, such as Azure Data Factory Integration Runtime, in the customer owned Azure subnet to access customer’s specific Windchill+ storage.
Steps to Share Information with PTC
Perform the following steps to share information with PTC.
1. Set up a subnet with Integration Runtime (IR) and configure it with the Microsoft storage service endpoint. For more information, see Azure virtual network service endpoints.
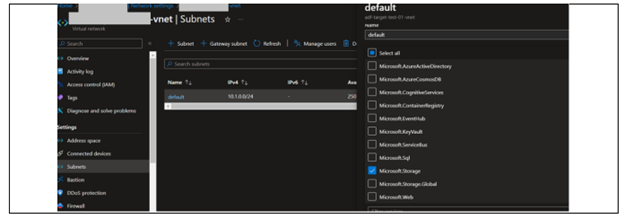
2. Submit a request to your IT or Azure administrators who manage the network. Request them to allow the subnet (set in the earlier step) to access PTC-managed storage account in a separate tenancy but within the same region.
◦ Run the following command in your Azure tenant subscription to obtain the subnet ID:
az network vnet subnet show --resource-group "customers_resource_group" --vnet-name "customers_vnet" --name "customers_subnet" --query id -- output tsv
The subnet ID is required by PTC to enable the connection from customer-specific subnet (no VPC peering is needed). For more information, see az network vnet subnet.
3. Open a service request with PTC to add the subnet ID from step 2 to the allow list. For more information see Opening a Service Request.
Upon successful completion of PTC Cloud service request, you can validate the access and implement the functionality in IR to retrieve your data exported from Windchill+ to your specific storage account.
Life cycle of Contents in ESI Shared Storage
• ESI response files shared in the ESI container are available for seven days for consumption by client applications.
• The response files are deleted after seven days.
• As a best practice, to keep storage clean and easy to manage, custom integrations should delete the response files after processing.
• The SAS token shared by PTC is valid for 365 days. You must submit a request to renew the token to continue running this integration.
• There is a separate ESI container for each environment.
• In case of a rehost, the same ESI container is available for use on the re-hosted system.