Step 7. Using ThingWorx OPC UA Mashups to Configure Your OPC UA Applications and Endpoints
To make the initial setup for the ThingWorx Azure IoT Hub Connector easier, there are a main mashup and three sub-mashups in ThingWorx Composer that you can use to discover OPC UA endpoints. You can then use the Industrial Connection mashup to bind properties to endpoints. Once you are set up and running, you can use ThingWorx Composer to view the Industrial Gateways and Industrial Connections and monitor telemetry.
When configuring OPC UA in ThingWorx, it may be helpful to understand the following concepts:
• Application — While this Microsoft Azure IIoT concept does not directly correlate to OPC UA, it is used in ThingWorx Composer for this integration. In the OPC UA landscape, every OPC UA Server has one application. In the OPC UA mashups in ThingWorx Composer, you provide the URL of an OPC UA Server that can enumerate OPC UA endpoints.
• Endpoint — "Endpoint" is an OPC UA term. One ThingWorx Kepware OPC UA Server can support multiple OPC UA endpoints. For example, consider this security-related use case for accepting remote OPC UA client connections: To achieve higher performance, define one endpoint that is bound to localhost with minimal security. For best security practices, define another endpoint that is bound to a network adapter with strict security when accepting remote OPC UA client connections.
• Application Type — The concept of application defines application types. The type of application that the ThingWorx Azure OPC UA integration uses is SERVER.
• Discovery URL — An OPC UA term, a Discovery URL is the URL address to an endpoint that can be used to discover other UA endpoints. This URL has a format similar to the following:
opc.tcp://{{OPCUAServer-IPADDRESS}}:{{OPCUAServer-PORT}}"
For example, the default port for ThingWorx Kepware Server is 49320. For information on KEPServerEX, refer to
Enabling the OPC UA Server in KEPServerEX for Remote OPC UA Client Access.
The following sections explain how to set up the OPC UA applications, endpoints in ThingWorx Composer. Click a section title to display its content. Click the title again to hide the content.
Link the AzureOpcUaConfiguration Mashup to Your AzureIotHubTemplate Thing
To configure your OPC UA Server/Application in ThingWorx, you use the AzureOpcUaConfiguration mashup. For quick access, you can link the mashup to your AzureIotHubTemplate Thing:
|
|
In the example screenshots shown in this procedure, the name of the AzureIotHubTemplate Thing is IIoTGateway.
|
1. Log in to ThingWorx Composer and navigate to your AzureIotHubTemplate Thing.
2. On the General page, scroll down until you see the field, Home Mashup.
3. From the dropdown, select the AzureOpcUaConfiguration mashup.
|
|
If you do not see these mashups in the list, it is likely that you have not set the opc-ua property to true in the configuration file for your Connector. You may see other errors as well if you do not have this property set to true.
|
The following figure shows the dropdown list of mashups within the IIoTGateway AzureIoTHubTemplate Thing UI.
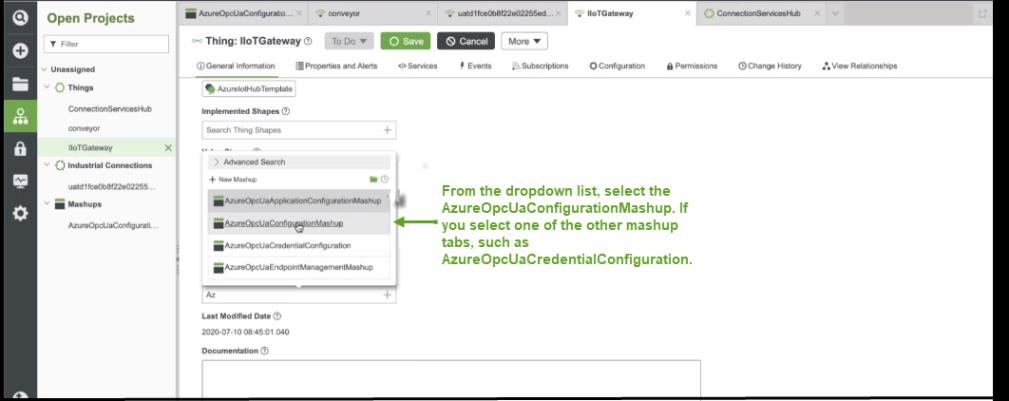
4. Click the Save button. When the page refreshes, the Mashup tab is available in the set of tabs. If you click the tab, the UI for the mashup appears, as shown here:
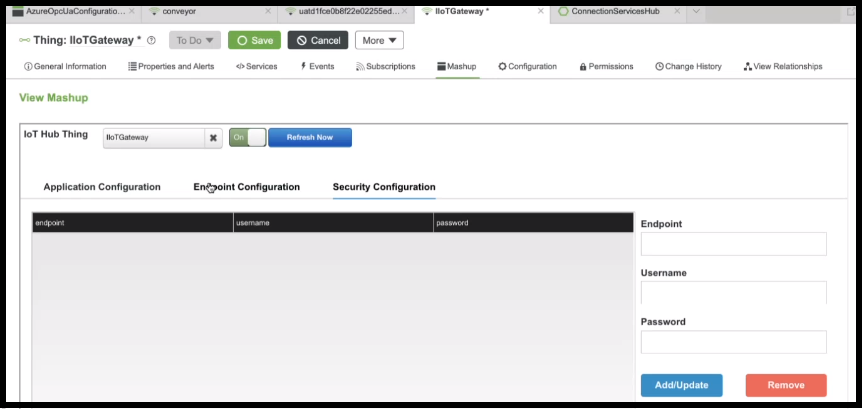
In the example above, the Security Configuration tab of the mashup is displayed. To add your application, click the Application Configuration tab and continue to the next section.
Application Configuration
To discover OPC UA endpoints for the OPC UA application from ThingWorx Composer, follow these steps:
1. If you have the AzureOpcUaConfiguration mashup displayed, skip this step. Otheriwse, in ThingWorx Composer, browse to your AzureIotHubTemplate Thing, and click the Mashup tab.
2. Click the Application Configuration tab, and in the Discovery Url field, supply the OPC UA address for the application, as shown here:
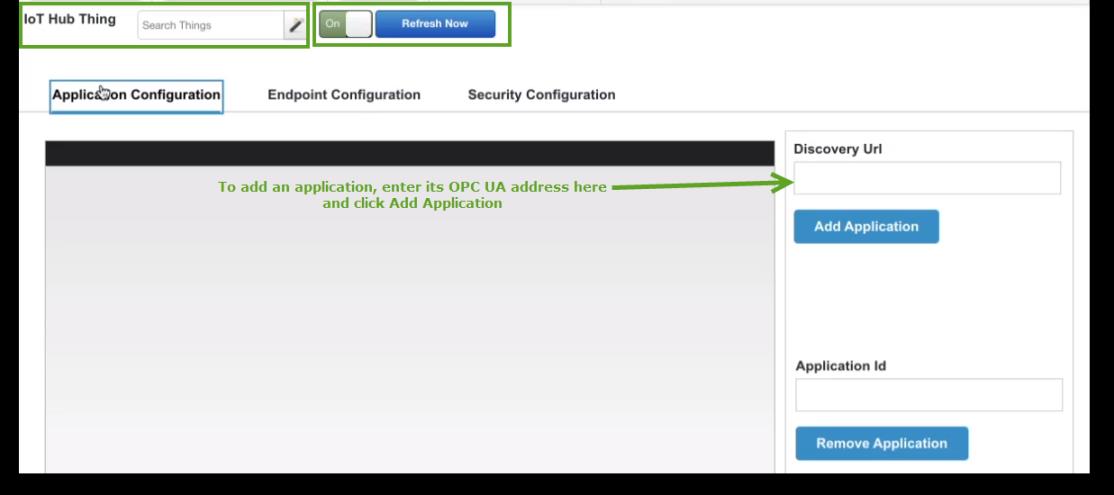
You can remove an application by copying the ApplicationId in the table, pasting it in the Application Id field, and then click Remove Application. |
Here is the Application Configuration list after two applications have been added:
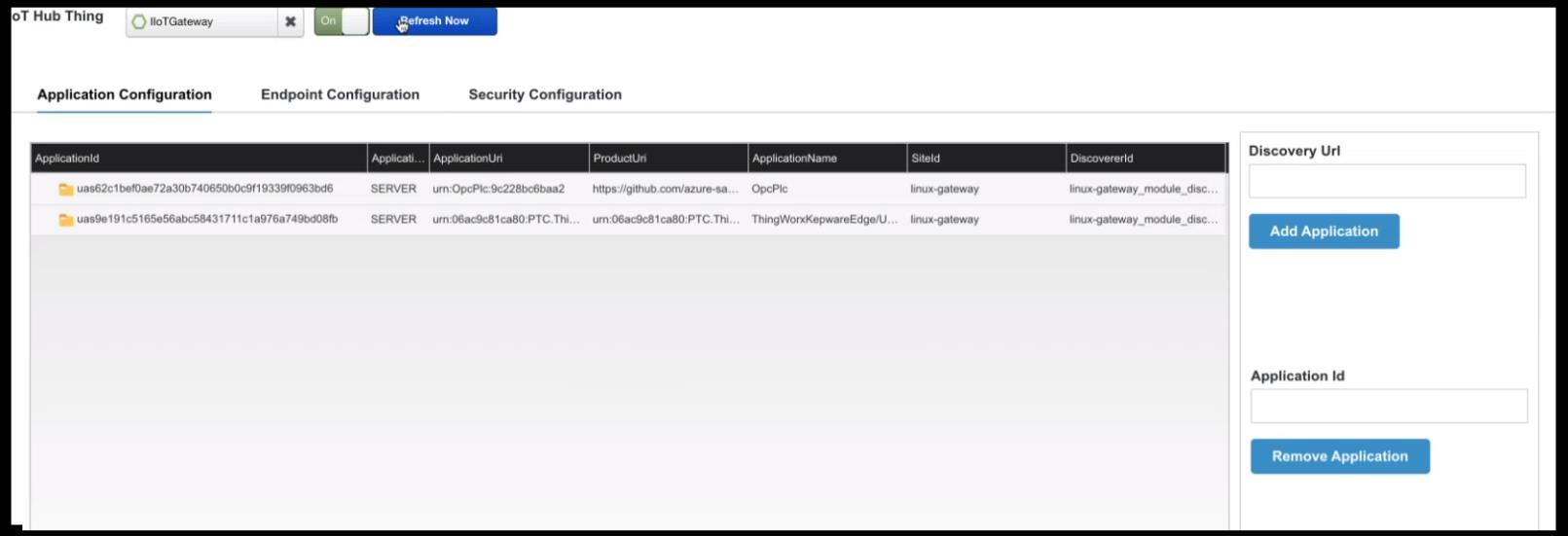
The table shows the following information for each application:
◦ ApplicationId — The unique identifier for the application returned by the Microsoft Azure Industrial IoT (IIoT) Microservices for the OPC UA Server. Each OPC UA Server has an application identifier (Id). These identifiers consist of alphanumeric characters only.
◦ Application Type — The type shown for the Azure OPC UA integration with ThingWorx Platform and Kepware is always SERVER.
◦ ApplicationUri — The URI of the application.
◦ ProductUri — The location of the product running the application.
◦ Application Name — The name of the application. If you are using ThingWorx Kepware Server (TKS), that name shows here, along with the unique id of the instance.
◦ SiteId — The operating system where the application is running.
◦ DiscoveredId — The identifier for the module.
Endpoint Configuration
After you add the application, the application is aware of the endpoints that are part of it. Every endpoint has a unique RegistrationId, which is returned by the Azure Industrial IoT (IIoT) Microservices. To help you see the mapping of the OPC UA Server's ApplicationId to its associated endpoints, the Endpoint Configuration page shows the ApplicationID in the column next to its RegistrationId.
ThingWorx gathers the credentials for endpoints and displays them in the Application Configuration, in the SecurityMode, SecurityPolicy, and AuthenticationMethods columns. The application may use either no authentication method or the Basic user name and password method.
In the following example one endpoint is shown for each application that has been added:
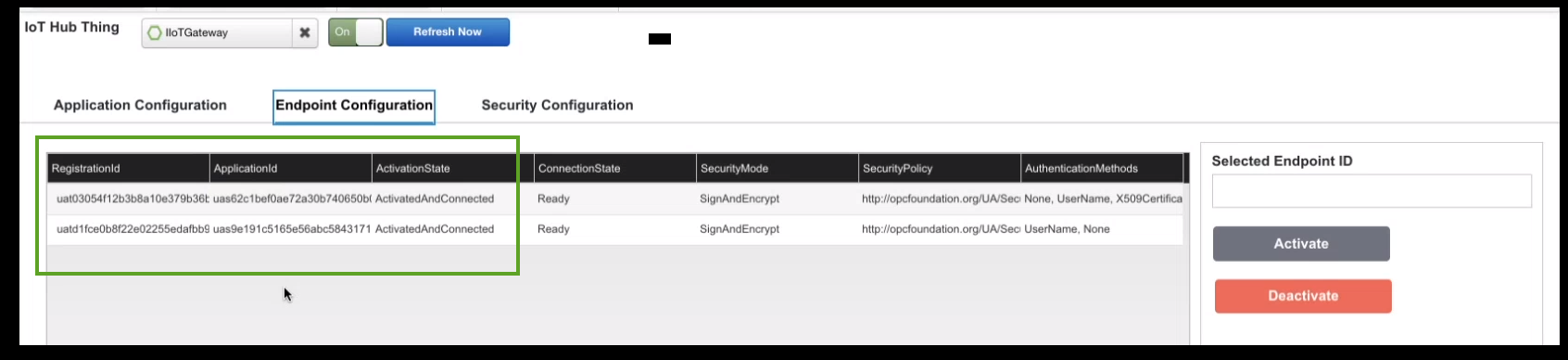
The Endpoint Configuration page shows all endpoints for all applications, not just those for an application selected in the Application Configuration page. This is the result of the Microsoft Azure OPC UA Stack implementation. One API discovers all the endpoints available for all applications that communicate with your Azure IoT Hub when you have multiple OPC UA servers registered. |
The third column highlighted in the figure above is the ActivationState. In this figure the endpoints have already been activated. However, when you are first adding the application, the endpoints are in a deactivated state. To enable the flow of telemetry to ThingWorx, you need to activate the endpoints for the application. If need be, you can always deactivate an endpoint to stop the flow of telemetry.
To activate or deactivate an endpoint:
1. On the Endpoint Configuration page, click the RegistrationId of the endpoint so that it appears in the field, Selected Endpoint ID.
2. Click the button for the action you want to take, Activate or Deactivate.
If the page does not update immediately, click Refresh Now. |
When the page refreshes and shows your change in the ActivationState column. The endpoint is ActivatedAndConnected. In addition, the ConnectionStart column is updated to Ready.
The other columns in the Endpoint Configuration page provide information about security as configured for the OPC UA Server/Application:
• SecurityMode — The mode SignAndEncrypt indicates that the messages are digitally signed and encrypted.
• SecurityPolicy — The security policy defined by the OPC Foundation, at the URL listed. This is not an Azure or ThingWorx security policy.
If an endpoint requires Basic authentication, continue to the next section to enter the user name and password.
Security Configuration
In the Endpoint Configuration page, you can see the security information for that endpoint. Different endpoints have different authentication methods, either Basic authentication or None.
Credentials are used for services that perform Command and Control operations on an OPC UA Server. The Azure Connector can pass the credential information that you configure in the Security Configuration page. Note that only Basic authentication and No authentication are the available options. For Basic authentication, you add a user name and password. Note that an empty password is allowed when a user name is specified.
If the authentication method is None, you do not need to specify credentials to perform Command and Control over the endpoint. However, if the endpoint has the ability to evaluate user name and password credentials, you can add the required user name and password that system will use to perform Command and Control over the endpoint in the Security Configuration page.
The ThingWorx side of the integration does not currently support X509 certificates and is therefore incompatible with endpoints that use X509. Only Basic authentication is supported. |
To add the credentials:
1. Click the Security Configuration tab to display the page.
2. In the Endpoint field supply the RegistrationId of the endpoint. You can copy it from the Endpoint Configuration page and paste it here.
3. In the Username field, type the user name to use to authenticate with this endpoint.
4. In the Password field, type the password to use to authenticate with this endpoint.
5. Click Add/Update. When the page refreshes, your security configuration appears in the table.
The system will use the configured user name and password to perform command and control over the endpoint and start publishing telemetry.
To remove the configuration, select the endpoint in the table. When the fields are populated, click Remove. |