SAML
Single Sign-On via SAML
Security Assertion Markup Language 2.0 (SAML 2.0) is a version of the SAML standard for exchanging authentication and authorization data between security domains. This allows Codebeamer to verify the identity of the end-user, based on the authentication performed by an Identity Provider, as well as to obtain basic profile information about the end-user.
Automatic SAML login is configured in > , by adding the following to the "saml" section:
"saml" : {
...
"automatic": false,
...
}
...
"automatic": false,
...
}
• true - Logging in automatically with SSO.
• false - Codebeamer login page appears. Users can choose to login with Codebeamer user credentials or with SSO.
See example Application Configurations below.
Interactive authentication at Web GUI
When interactively accessing the Codebeamer Web GUI via a Web Browser, Codebeamer will act as the Service Provider in the SAML Authorization Code Flow:
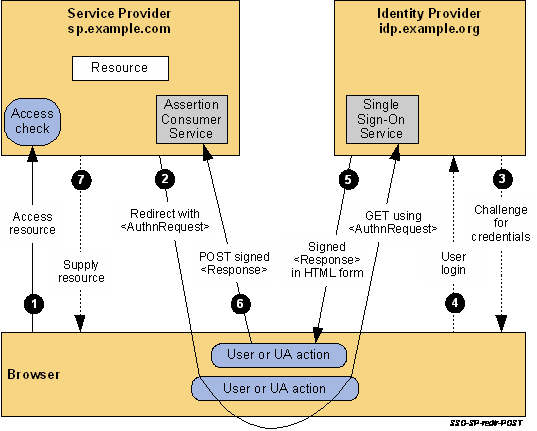
The authentication and authorization GUI is solely provided by the Identity Provider. See Google example below
The Codebeamer Login Page will not be used and Codebeamer will also never know the credentials of the authenticated users.
If there is no account for an authenticated user yet, a new account will be created with the user information provided by the Identity Provider, and default settings for:
• User Licenses.
• User Group Memberships.
User account matching is done via the first non-empty value of the following Assertion attribute:
• ssoId
• name
• email
Any space in the resulting Codebeamer user account name will be removed.
An interactive user logout at Codebeamer will:
• Revoke the user session.
• Redirect the user to the Codebeamer login page.
Sign In with Google - Example
When SAML SSO is configured, the option to authenticate by external domain will appear.

When using Google as Identity Provider, standard Google Web Single Sign-On will be applied, where you first have to enter you username/email and then your password:
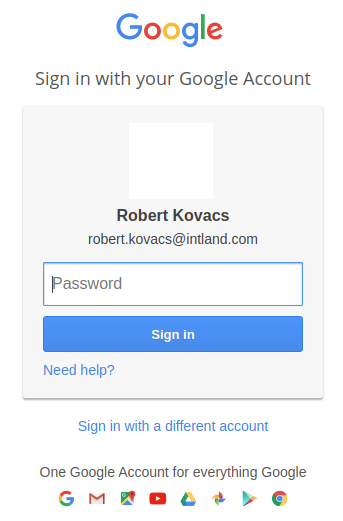
Clicking Next on the second screen will redirect to Codebeamer, where users are logged in with their Google account.

REST-API authentication
SAML does not support REST-API authentication, standard authentication (username/password) has to be used in these cases.
SAML Identity Provider
System Administrators can choose public Identity Providers, e.g.
• Google
• SSOCircle
• ADFS
One Codebeamer instance can only have a single SAML Identity Provider.
SAML Identity Provider example - Google
To setup Google as Identity Provider the following steps are needed.
1. Open Google Admin UI.

2. Open Application Configuration UI.

3. Open SAML Application configuration UI.

4. Click plus sign (Enable SSO for SAML Application) and click Setup my own custom app.

5. Google IdP Information: Entity ID, URLs and keys are automatically generated. Download IDP metadata, by clicking the Download button in the bottom section:

6. Name application. Optionally add Description and Upload Logo.

7. Add ACS URL and Entity ID. Check Signed Response and accept default Name ID attribute mapping. Assertion Consumer Service needs to use HTTPS protocol.

8. Add mapping to various user attributes.

9. Click Finish.
10. Enable service for everyone or selected members:

SAML Identity Provider example - SSOCircle
Follow these steps to setup SSOCircle as Identity Provider:
1. Download Codebeamer SP metadata from metadata endpoint (<codebeamer base-URL>/saml/sp/metadata).
2. Remove <ds:Signature> tag from metadata .xml file.
3. Open SSOCircle, and go to Manage Metadata.
4. Click [Add new Service Provider], and fill the Service Provider Entity ID, metadata .xml file location, and user attributes to send with SAML Assertion.
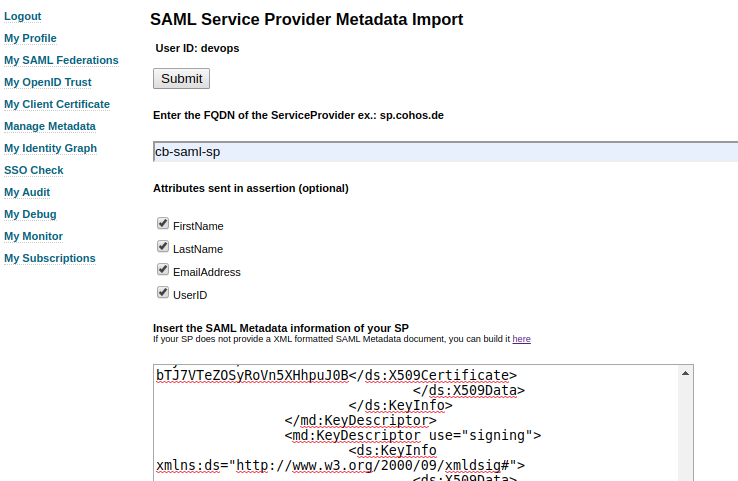
5. Download IDP metadata.
6. Remove HTTP Redirect from AssertionConsumerService endpoints: <!-- <SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://idp.ssocircle.com:443/sso/SSORedirect/metaAlias/publicidp"/> --> <SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://idp.ssocircle.com:443/sso/SSOPOST/metaAlias/publicidp"/>
7. Upload IDP .xml file to Codebeamer into SAML configuration.
SAML Identity Provider example - ADFS
Follow these steps to configure ADFS as Identity Provider:
1. Open Active Directory Federation Services Manager.
2. Click Add Relaying Party Trust.
3. Choose Claim aware option on the welcome page.
4. Either use the metadata URL of Codebeamer metadata provider, or attach the downloaded Service Provider .xml file:

5. Add a Name and Description to the IDP.
6. Choose who can use SAML login with the access control policy.
7. Review configuration and finish.
8. Click Edit Claim Issue Policy for the new IDP.
9. Configure how the claims are satisfied (see User mapping configuration section), as an example test the following 2 rules are used:

This configures the claim mapping.

This will satisfy the mandatory name identifier: c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"] => issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress");
10. Restart Codebeamer service and test configuration.
SAML Service Provider
In the current SAML flow Codebeamer takes the Service Provider role. Following the 2 example IDP configuration in Codebeamer.
Check SAML configuration section to understand how these configurations work.
SAML Service Provider example - Google
"saml": {
"allowSignUp": true,
"automatic": false,
"enabled": true,
"domain": "intland.com",
"idp": {
"entityId": "https://accounts.google.com/o/saml2?idpid=C025kbbvq",
"url": "",
"xml": "<?xml version=\"1.0\" encoding=\"UTF-8\" standalone=\"no\"?>\r\n<md:EntityDescriptor xmlns:md=\"urn:oasis:names:tc:SAML:2.0:metadata\" entityID=\"https://accounts.google.com/o/saml2?idpid=C025kbbvq\" validUntil=\"2024-10-08T11:46:30.000Z\">\r\n <md:IDPSSODescriptor WantAuthnRequestsSigned=\"false\" protocolSupportEnumeration=\"urn:oasis:names:tc:SAML:2.0:protocol\">\r\n <md:KeyDescriptor use=\"signing\">\r\n <ds:KeyInfo xmlns:ds=\"http://www.w3.org/2000/09/xmldsig#\">\r\n <ds:X509Data>\r\n <ds:X509Certificate>MIIDdDCCAlygAwIBAgIGAW21feyGMA0GCSqGSIb3DQEBCwUAMHsxFDASBgNVBAoTC0dvb2dsZSBJ\r\nbmMuMRYwFAYDVQQHEw1Nb3VudGFpbiBWaWV3MQ8wDQYDVQQDEwZHb29nbGUxGDAWBgNVBAsTD0dv\r\nb2dsZSBGb3IgV29yazELMAkGA1UEBhMCVVMxEzARBgNVBAgTCkNhbGlmb3JuaWEwHhcNMTkxMDEw\r\nMTE0NjMwWhcNMjQxMDA4MTE0NjMwWjB7MRQwEgYDVQQKEwtHb29nbGUgSW5jLjEWMBQGA1UEBxMN\r\nTW91bnRhaW4gVmlldzEPMA0GA1UEAxMGR29vZ2xlMRgwFgYDVQQLEw9Hb29nbGUgRm9yIFdvcmsx\r\nCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpDYWxpZm9ybmlhMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A\r\nMIIBCgKCAQEA5Yz9Ceh3w6VwdBnd5SsLUGkvvUNcGuZCG3A+g08PWWtDNqnjh1fPsvkY5FQ//fd1\r\n4KMF92DbKu77D3VFE+snFiBOggku3e6Nl1omSGerpgvb1BLX1MD6MBR2eySKAyHUh+vFjvRGwGjo\r\nKphyiomKCi6dVg+lsj7mU/5dh8+QW2EekJCrRaH0Mr9QBYdhfUNFgTNT+9Aj41bTjbuvNmSXgz+Y\r\nqXu+5fbjaXwzuBnDw/LS48Q23L8FLPP21ynit8T3nkzzXj/k4ju2Iz7T0YbYyN6U1on7oJBO+0YW\r\nIib+y3Q1yNd7O2/fPBgiNdCg2GI0M9rRggBuWOtdsDBHTHAQRQIDAQABMA0GCSqGSIb3DQEBCwUA\r\nA4IBAQCuRxSsNZtZjdWws/ase3+SXePX2INU4nQwlZejzXdygwOpwNPbtzxjDOZbXAAgLLGWh6h5\r\n+Gcgx62q5R+b6VSiV712zuFZ00rO9hhvbGFtT3EOeSKxUdi3LT5n+zC5bJOnlbgY3rxJOcEyHiTN\r\n7S2/ZJXMJlwQ0n9nZw94YF7rqTC4m3ZoiCf0iJOMYDsfywxLciRpDulBmsotwCtWyMBaTygSWDlf\r\nEPHuZfWrWrkppWPhchmbq5wiPJicK0droSSGUNmpZF/oULgGj5f8sx/QrfvDPzeDQC68cq0VAC1o\r\nXG3BCay0nM8JvRJ1V3k4GFbK8ZV8qlSE6Xye/ernmkl/</ds:X509Certificate>\r\n </ds:X509Data>\r\n </ds:KeyInfo>\r\n </md:KeyDescriptor>\r\n <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>\r\n <md:SingleSignOnService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect\" Location=\"https://accounts.google.com/o/saml2/idp?idpid=C025kbbvq\"/>\r\n <md:SingleSignOnService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST\" Location=\"https://accounts.google.com/o/saml2/idp?idpid=C025kbbvq\"/>\r\n </md:IDPSSODescriptor>\r\n</md:EntityDescriptor>"
},
"sp": {
"activeKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCuVzyqFgMSyDANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDMwNDRaFw0yODA1\nMTExNDMwNDRaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDRu7/EI0BlNzMEBFVAcbx+lLos\nvzIWU+01dGTY8gBdhMQNYKZ92lMceo2CuVJ66cUURPym3i7nGGzoSnAxAre+0YIM\n+U0razrWtAUE735bkcqELZkOTZLelaoOztmWqRbe5OuEmpewH7cx+kNgcVjdctOG\ny3Q6x+I4qakY/9qhBQIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAAeViTvHOyQopWEi\nXOfI2Z9eukwrSknDwq/zscR0YxwwqDBMt/QdAODfSwAfnciiYLkmEjlozWRtOeN+\nqK7UFgP1bRl5qksrYX5S0z2iGJh0GvonLUt3e20Ssfl5tTEDDnAEUMLfBkyaxEHD\nRZ/nbTJ7VTeZOSyRoVn5XHhpuJ0B\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,7C8510E4CED17A9F\n\nSRYezKuY+AgM+gdiklVDBQ1ljeCFKnW3c5BM9sEyEOfkQm0zZx6fLr0afup0ToE4\niJGLxKw8swAnUAIjYda9wxqIEBb9mILyuRPevyfzmio2lE9KnARDEYRBqbwD9Lpd\nvwZKNGHHJbZAgcUNfhXiYakmx0cUyp8HeO3Vqa/0XMiI/HAdlJ/ruYeT4e2DSrz9\nORZA2S5OvNpRQeCVf26l6ODKXnkDL0t5fDVY4lAhaiyhZtoT0sADlPIERBw73kHm\nfGCTniY9qT0DT+R5Rqukk42mN2ij/cAr+kdV5colBi1fuN6d9gawCiH4zSb3LzHQ\n9ccSlz6iQV1Ty2cRuTkB3zWC6Oy4q0BRlXnVRFOnOfYJztO6c2hD3Q9NxkDAbcgR\nYWJWHpd0/HI8GyBpOG7hAS1l6aoleH30QCDOo7N2rFrTAaPC6g84oZOFSqkqvx4R\nKTbWRwgJsqVxM6GqV6H9x1LNn2CpBizdGnp8VvnIiYcEvItMJbT1C1yeIUPoDDU2\nCt0Jofw/dquXStHWftPFjpIqB+5Ou//HQ2VNzjbyThNWVGtjnEKwSiHacQLS1sB3\niqFtSN/VCpdOcRujEBba+x5vlc8XCV1qr6x1PbvfPZVjyFdSM6JQidr0uEeDGDW3\nTuYC1YgURN8zh0QF2lJIMX3xgbhr8HHNXv60ulcjeqYmna6VCS8AKJQgRTr4DGWt\nAfv9BFV943Yp3nHwPC7nYC4FvMxOn4qW4KrHRJl57zcY6VDL4J030CfmvLjqUbuT\nLYiQp/YgFlmoE4bcGuCiaRfUJZCwooPK2dQMoIvMZeVl9ExUGdXVMg==\n-----END RSA PRIVATE KEY-----"
},
"entityId": "cb-saml-sp",
"signMetadata": true,
"signRequests": true,
"standbyKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCQqf5mvKPOpzANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDQ0NDZaFw0yODA1\nMTExNDQ0NDZaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCXJXpaDE6QmY9eN9pwcG8k/54a\nK9YLzRgln64hZ6mvdK+OIIBB5E2Pgenfc3Pi8pF0B9dGUbbNK8+8L6HcZRT/3aXM\nWlJsENJdMS13pnmSFimsTqoxYnayc2EaHULtvhMvLKf7UPRwX4jzxLanc6R4IcUL\nJZ/dg9gBT5KDlm164wIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAHDyh2B4AZ1C9LSi\ngis+sAiVJIzODsnKg8pIWGI7bcFUK+i/Vj7qlx09ZD/GbrQts87Yp4aq+5OqVqb5\nn6bS8DWB8jHCoHC5HACSBb3J7x/mC0PBsKXA9A8NSFzScErvfD/ACjWg3DJEghxn\nlqAVTm/DQX/t8kNTdrLdlzsYTuE0\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,393409C5B5DFA31D\n\nO40s+E7P75d8OOcfvE3HTNY8gsULhYk7SBdRw50ZklH5G/TZwCxxfoRfPiA4Q1Jf\nbpEHF8BzyLzjXZwYJT5UqaXW/3ozMj7BZ95UfCR0hrxMXQWq4Nak6gFyHh/1focS\nljzsLoBjyqjCc4BiFPD8uQHVGFv/PttCLydshnAVdSSrFLi0kVsFJMYOmL9ILG6l\nLd7Sb2ayD0/+1L0lLW8F6IbTtEYAwuA+mX25Imr9JMPKem1YwI1pqUHr8ifq0kd+\nJsoI4Q0Qf2CKv/nfZI5EjqJO34U5podj2zkqN1W3z7dzdTYNOmigq8XVrBiSmT8B\nlE7Ea1GDFol90AeF6ltJWEE6rM6kYzOoModXdK0ozEu4JNnBV/Fu81sOV9zHBs+9\nzqM7jCC16b6n5W2IKGad02GVCBKE0fmIEfhEUsTJw5UJLjNFYF2PkA13Y7jVGZMT\n38MfE3gWcYYOhXVPuMvJ1thXbjXEImg3yH+XHN3RMyups2B1s2JAXYVP2n5zI9pS\nY3Wt6iXAkKJ0Fiaa/myitUGtL1QvbhBOOfsw9HFuesxzJuKTJ7gqs0ceYwtpQ4X8\nwjk0HXz/riAb+BI6ImEd6H077e/U5u1c9WOdqAKEExAlXL8EhG5Azsj84cCAFuGl\n+T5XVBir0a1jUBQycnsinGZoy3lhE+92j8EhM4LgrDbzoqICVLrk1jX9FiDbcqzZ\nif87phEJmxz+ymCygUjzYohc0sIOwVcMl+s6Y+JsfSBDyg2XEIhzPPdGdgpCrxBg\nKEtaNgtbHXo7UOlN6voWliM14n1g13+xtUuX7hRve3Uy7MMwtuSVJA==\n-----END RSA PRIVATE KEY-----"
},
"wantAssertionsSigned": true
},
"user": {
"email": "email",
"firstName": "firstname",
"lastName": "lastname",
"name": "email",
"ssoId": "email"
}
}
"allowSignUp": true,
"automatic": false,
"enabled": true,
"domain": "intland.com",
"idp": {
"entityId": "https://accounts.google.com/o/saml2?idpid=C025kbbvq",
"url": "",
"xml": "<?xml version=\"1.0\" encoding=\"UTF-8\" standalone=\"no\"?>\r\n<md:EntityDescriptor xmlns:md=\"urn:oasis:names:tc:SAML:2.0:metadata\" entityID=\"https://accounts.google.com/o/saml2?idpid=C025kbbvq\" validUntil=\"2024-10-08T11:46:30.000Z\">\r\n <md:IDPSSODescriptor WantAuthnRequestsSigned=\"false\" protocolSupportEnumeration=\"urn:oasis:names:tc:SAML:2.0:protocol\">\r\n <md:KeyDescriptor use=\"signing\">\r\n <ds:KeyInfo xmlns:ds=\"http://www.w3.org/2000/09/xmldsig#\">\r\n <ds:X509Data>\r\n <ds:X509Certificate>MIIDdDCCAlygAwIBAgIGAW21feyGMA0GCSqGSIb3DQEBCwUAMHsxFDASBgNVBAoTC0dvb2dsZSBJ\r\nbmMuMRYwFAYDVQQHEw1Nb3VudGFpbiBWaWV3MQ8wDQYDVQQDEwZHb29nbGUxGDAWBgNVBAsTD0dv\r\nb2dsZSBGb3IgV29yazELMAkGA1UEBhMCVVMxEzARBgNVBAgTCkNhbGlmb3JuaWEwHhcNMTkxMDEw\r\nMTE0NjMwWhcNMjQxMDA4MTE0NjMwWjB7MRQwEgYDVQQKEwtHb29nbGUgSW5jLjEWMBQGA1UEBxMN\r\nTW91bnRhaW4gVmlldzEPMA0GA1UEAxMGR29vZ2xlMRgwFgYDVQQLEw9Hb29nbGUgRm9yIFdvcmsx\r\nCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpDYWxpZm9ybmlhMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A\r\nMIIBCgKCAQEA5Yz9Ceh3w6VwdBnd5SsLUGkvvUNcGuZCG3A+g08PWWtDNqnjh1fPsvkY5FQ//fd1\r\n4KMF92DbKu77D3VFE+snFiBOggku3e6Nl1omSGerpgvb1BLX1MD6MBR2eySKAyHUh+vFjvRGwGjo\r\nKphyiomKCi6dVg+lsj7mU/5dh8+QW2EekJCrRaH0Mr9QBYdhfUNFgTNT+9Aj41bTjbuvNmSXgz+Y\r\nqXu+5fbjaXwzuBnDw/LS48Q23L8FLPP21ynit8T3nkzzXj/k4ju2Iz7T0YbYyN6U1on7oJBO+0YW\r\nIib+y3Q1yNd7O2/fPBgiNdCg2GI0M9rRggBuWOtdsDBHTHAQRQIDAQABMA0GCSqGSIb3DQEBCwUA\r\nA4IBAQCuRxSsNZtZjdWws/ase3+SXePX2INU4nQwlZejzXdygwOpwNPbtzxjDOZbXAAgLLGWh6h5\r\n+Gcgx62q5R+b6VSiV712zuFZ00rO9hhvbGFtT3EOeSKxUdi3LT5n+zC5bJOnlbgY3rxJOcEyHiTN\r\n7S2/ZJXMJlwQ0n9nZw94YF7rqTC4m3ZoiCf0iJOMYDsfywxLciRpDulBmsotwCtWyMBaTygSWDlf\r\nEPHuZfWrWrkppWPhchmbq5wiPJicK0droSSGUNmpZF/oULgGj5f8sx/QrfvDPzeDQC68cq0VAC1o\r\nXG3BCay0nM8JvRJ1V3k4GFbK8ZV8qlSE6Xye/ernmkl/</ds:X509Certificate>\r\n </ds:X509Data>\r\n </ds:KeyInfo>\r\n </md:KeyDescriptor>\r\n <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>\r\n <md:SingleSignOnService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect\" Location=\"https://accounts.google.com/o/saml2/idp?idpid=C025kbbvq\"/>\r\n <md:SingleSignOnService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST\" Location=\"https://accounts.google.com/o/saml2/idp?idpid=C025kbbvq\"/>\r\n </md:IDPSSODescriptor>\r\n</md:EntityDescriptor>"
},
"sp": {
"activeKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCuVzyqFgMSyDANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDMwNDRaFw0yODA1\nMTExNDMwNDRaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDRu7/EI0BlNzMEBFVAcbx+lLos\nvzIWU+01dGTY8gBdhMQNYKZ92lMceo2CuVJ66cUURPym3i7nGGzoSnAxAre+0YIM\n+U0razrWtAUE735bkcqELZkOTZLelaoOztmWqRbe5OuEmpewH7cx+kNgcVjdctOG\ny3Q6x+I4qakY/9qhBQIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAAeViTvHOyQopWEi\nXOfI2Z9eukwrSknDwq/zscR0YxwwqDBMt/QdAODfSwAfnciiYLkmEjlozWRtOeN+\nqK7UFgP1bRl5qksrYX5S0z2iGJh0GvonLUt3e20Ssfl5tTEDDnAEUMLfBkyaxEHD\nRZ/nbTJ7VTeZOSyRoVn5XHhpuJ0B\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,7C8510E4CED17A9F\n\nSRYezKuY+AgM+gdiklVDBQ1ljeCFKnW3c5BM9sEyEOfkQm0zZx6fLr0afup0ToE4\niJGLxKw8swAnUAIjYda9wxqIEBb9mILyuRPevyfzmio2lE9KnARDEYRBqbwD9Lpd\nvwZKNGHHJbZAgcUNfhXiYakmx0cUyp8HeO3Vqa/0XMiI/HAdlJ/ruYeT4e2DSrz9\nORZA2S5OvNpRQeCVf26l6ODKXnkDL0t5fDVY4lAhaiyhZtoT0sADlPIERBw73kHm\nfGCTniY9qT0DT+R5Rqukk42mN2ij/cAr+kdV5colBi1fuN6d9gawCiH4zSb3LzHQ\n9ccSlz6iQV1Ty2cRuTkB3zWC6Oy4q0BRlXnVRFOnOfYJztO6c2hD3Q9NxkDAbcgR\nYWJWHpd0/HI8GyBpOG7hAS1l6aoleH30QCDOo7N2rFrTAaPC6g84oZOFSqkqvx4R\nKTbWRwgJsqVxM6GqV6H9x1LNn2CpBizdGnp8VvnIiYcEvItMJbT1C1yeIUPoDDU2\nCt0Jofw/dquXStHWftPFjpIqB+5Ou//HQ2VNzjbyThNWVGtjnEKwSiHacQLS1sB3\niqFtSN/VCpdOcRujEBba+x5vlc8XCV1qr6x1PbvfPZVjyFdSM6JQidr0uEeDGDW3\nTuYC1YgURN8zh0QF2lJIMX3xgbhr8HHNXv60ulcjeqYmna6VCS8AKJQgRTr4DGWt\nAfv9BFV943Yp3nHwPC7nYC4FvMxOn4qW4KrHRJl57zcY6VDL4J030CfmvLjqUbuT\nLYiQp/YgFlmoE4bcGuCiaRfUJZCwooPK2dQMoIvMZeVl9ExUGdXVMg==\n-----END RSA PRIVATE KEY-----"
},
"entityId": "cb-saml-sp",
"signMetadata": true,
"signRequests": true,
"standbyKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCQqf5mvKPOpzANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDQ0NDZaFw0yODA1\nMTExNDQ0NDZaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCXJXpaDE6QmY9eN9pwcG8k/54a\nK9YLzRgln64hZ6mvdK+OIIBB5E2Pgenfc3Pi8pF0B9dGUbbNK8+8L6HcZRT/3aXM\nWlJsENJdMS13pnmSFimsTqoxYnayc2EaHULtvhMvLKf7UPRwX4jzxLanc6R4IcUL\nJZ/dg9gBT5KDlm164wIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAHDyh2B4AZ1C9LSi\ngis+sAiVJIzODsnKg8pIWGI7bcFUK+i/Vj7qlx09ZD/GbrQts87Yp4aq+5OqVqb5\nn6bS8DWB8jHCoHC5HACSBb3J7x/mC0PBsKXA9A8NSFzScErvfD/ACjWg3DJEghxn\nlqAVTm/DQX/t8kNTdrLdlzsYTuE0\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,393409C5B5DFA31D\n\nO40s+E7P75d8OOcfvE3HTNY8gsULhYk7SBdRw50ZklH5G/TZwCxxfoRfPiA4Q1Jf\nbpEHF8BzyLzjXZwYJT5UqaXW/3ozMj7BZ95UfCR0hrxMXQWq4Nak6gFyHh/1focS\nljzsLoBjyqjCc4BiFPD8uQHVGFv/PttCLydshnAVdSSrFLi0kVsFJMYOmL9ILG6l\nLd7Sb2ayD0/+1L0lLW8F6IbTtEYAwuA+mX25Imr9JMPKem1YwI1pqUHr8ifq0kd+\nJsoI4Q0Qf2CKv/nfZI5EjqJO34U5podj2zkqN1W3z7dzdTYNOmigq8XVrBiSmT8B\nlE7Ea1GDFol90AeF6ltJWEE6rM6kYzOoModXdK0ozEu4JNnBV/Fu81sOV9zHBs+9\nzqM7jCC16b6n5W2IKGad02GVCBKE0fmIEfhEUsTJw5UJLjNFYF2PkA13Y7jVGZMT\n38MfE3gWcYYOhXVPuMvJ1thXbjXEImg3yH+XHN3RMyups2B1s2JAXYVP2n5zI9pS\nY3Wt6iXAkKJ0Fiaa/myitUGtL1QvbhBOOfsw9HFuesxzJuKTJ7gqs0ceYwtpQ4X8\nwjk0HXz/riAb+BI6ImEd6H077e/U5u1c9WOdqAKEExAlXL8EhG5Azsj84cCAFuGl\n+T5XVBir0a1jUBQycnsinGZoy3lhE+92j8EhM4LgrDbzoqICVLrk1jX9FiDbcqzZ\nif87phEJmxz+ymCygUjzYohc0sIOwVcMl+s6Y+JsfSBDyg2XEIhzPPdGdgpCrxBg\nKEtaNgtbHXo7UOlN6voWliM14n1g13+xtUuX7hRve3Uy7MMwtuSVJA==\n-----END RSA PRIVATE KEY-----"
},
"wantAssertionsSigned": true
},
"user": {
"email": "email",
"firstName": "firstname",
"lastName": "lastname",
"name": "email",
"ssoId": "email"
}
}
Google SSO only works over HTTPS and only with your domain. |
SAML Service Provider example - SSOCircle
"saml": {
"allowSignUp": true,
"automatic": false,
"enabled": true,
"domain": "intland.com",
"idp": {
"entityId": "https://idp.ssocircle.com",
"url": "",
"xml": "<?xml version=\"1.0\" encoding=\"UTF-8\" standalone=\"yes\"?>\r\n<EntityDescriptor entityID=\"https://idp.ssocircle.com\" xmlns=\"urn:oasis:names:tc:SAML:2.0:metadata\">\r\n <IDPSSODescriptor WantAuthnRequestsSigned=\"false\" protocolSupportEnumeration=\"urn:oasis:names:tc:SAML:2.0:protocol\">\r\n <KeyDescriptor use=\"signing\">\r\n <ds:KeyInfo xmlns:ds=\"http://www.w3.org/2000/09/xmldsig#\">\r\n <ds:X509Data>\r\n <ds:X509Certificate>\r\nMIIEYzCCAkugAwIBAgIDIAZmMA0GCSqGSIb3DQEBCwUAMC4xCzAJBgNVBAYTAkRF\r\nMRIwEAYDVQQKDAlTU09DaXJjbGUxCzAJBgNVBAMMAkNBMB4XDTE2MDgwMzE1MDMy\r\nM1oXDTI2MDMwNDE1MDMyM1owPTELMAkGA1UEBhMCREUxEjAQBgNVBAoTCVNTT0Np\r\ncmNsZTEaMBgGA1UEAxMRaWRwLnNzb2NpcmNsZS5jb20wggEiMA0GCSqGSIb3DQEB\r\nAQUAA4IBDwAwggEKAoIBAQCAwWJyOYhYmWZF2TJvm1VyZccs3ZJ0TsNcoazr2pTW\r\ncY8WTRbIV9d06zYjngvWibyiylewGXcYONB106ZNUdNgrmFd5194Wsyx6bPvnjZE\r\nERny9LOfuwQaqDYeKhI6c+veXApnOfsY26u9Lqb9sga9JnCkUGRaoVrAVM3yfghv\r\n/Cg/QEg+I6SVES75tKdcLDTt/FwmAYDEBV8l52bcMDNF+JWtAuetI9/dWCBe9VTC\r\nasAr2Fxw1ZYTAiqGI9sW4kWS2ApedbqsgH3qqMlPA7tg9iKy8Yw/deEn0qQIx8Gl\r\nVnQFpDgzG9k+jwBoebAYfGvMcO/BDXD2pbWTN+DvbURlAgMBAAGjezB5MAkGA1Ud\r\nEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmlj\r\nYXRlMB0GA1UdDgQWBBQhAmCewE7aonAvyJfjImCRZDtccTAfBgNVHSMEGDAWgBTA\r\n1nEA+0za6ppLItkOX5yEp8cQaTANBgkqhkiG9w0BAQsFAAOCAgEAAhC5/WsF9ztJ\r\nHgo+x9KV9bqVS0MmsgpG26yOAqFYwOSPmUuYmJmHgmKGjKrj1fdCINtzcBHFFBC1\r\nmaGJ33lMk2bM2THx22/O93f4RFnFab7t23jRFcF0amQUOsDvltfJw7XCal8JdgPU\r\ng6TNC4Fy9XYv0OAHc3oDp3vl1Yj8/1qBg6Rc39kehmD5v8SKYmpE7yFKxDF1ol9D\r\nKDG/LvClSvnuVP0b4BWdBAA9aJSFtdNGgEvpEUqGkJ1osLVqCMvSYsUtHmapaX3h\r\niM9RbX38jsSgsl44Rar5Ioc7KXOOZFGfEKyyUqucYpjWCOXJELAVAzp7XTvA2q55\r\nu31hO0w8Yx4uEQKlmxDuZmxpMz4EWARyjHSAuDKEW1RJvUr6+5uA9qeOKxLiKN1j\r\no6eWAcl6Wr9MreXR9kFpS6kHllfdVSrJES4ST0uh1Jp4EYgmiyMmFCbUpKXifpsN\r\nWCLDenE3hllF0+q3wIdu+4P82RIM71n7qVgnDnK29wnLhHDat9rkC62CIbonpkVY\r\nmnReX0jze+7twRanJOMCJ+lFg16BDvBcG8u0n/wIDkHHitBI7bU1k6c6DydLQ+69\r\nh8SCo6sO9YuD+/3xAGKad4ImZ6vTwlB4zDCpu6YgQWocWRXE+VkOb+RBfvP755PU\r\naLfL63AFVlpOnEpIio5++UjNJRuPuAA=\r\n </ds:X509Certificate>\r\n </ds:X509Data>\r\n </ds:KeyInfo>\r\n </KeyDescriptor>\r\n <KeyDescriptor use=\"encryption\">\r\n <ds:KeyInfo xmlns:ds=\"http://www.w3.org/2000/09/xmldsig#\">\r\n <ds:X509Data>\r\n <ds:X509Certificate>\r\nMIIEYzCCAkugAwIBAgIDIAZmMA0GCSqGSIb3DQEBCwUAMC4xCzAJBgNVBAYTAkRF\r\nMRIwEAYDVQQKDAlTU09DaXJjbGUxCzAJBgNVBAMMAkNBMB4XDTE2MDgwMzE1MDMy\r\nM1oXDTI2MDMwNDE1MDMyM1owPTELMAkGA1UEBhMCREUxEjAQBgNVBAoTCVNTT0Np\r\ncmNsZTEaMBgGA1UEAxMRaWRwLnNzb2NpcmNsZS5jb20wggEiMA0GCSqGSIb3DQEB\r\nAQUAA4IBDwAwggEKAoIBAQCAwWJyOYhYmWZF2TJvm1VyZccs3ZJ0TsNcoazr2pTW\r\ncY8WTRbIV9d06zYjngvWibyiylewGXcYONB106ZNUdNgrmFd5194Wsyx6bPvnjZE\r\nERny9LOfuwQaqDYeKhI6c+veXApnOfsY26u9Lqb9sga9JnCkUGRaoVrAVM3yfghv\r\n/Cg/QEg+I6SVES75tKdcLDTt/FwmAYDEBV8l52bcMDNF+JWtAuetI9/dWCBe9VTC\r\nasAr2Fxw1ZYTAiqGI9sW4kWS2ApedbqsgH3qqMlPA7tg9iKy8Yw/deEn0qQIx8Gl\r\nVnQFpDgzG9k+jwBoebAYfGvMcO/BDXD2pbWTN+DvbURlAgMBAAGjezB5MAkGA1Ud\r\nEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmlj\r\nYXRlMB0GA1UdDgQWBBQhAmCewE7aonAvyJfjImCRZDtccTAfBgNVHSMEGDAWgBTA\r\n1nEA+0za6ppLItkOX5yEp8cQaTANBgkqhkiG9w0BAQsFAAOCAgEAAhC5/WsF9ztJ\r\nHgo+x9KV9bqVS0MmsgpG26yOAqFYwOSPmUuYmJmHgmKGjKrj1fdCINtzcBHFFBC1\r\nmaGJ33lMk2bM2THx22/O93f4RFnFab7t23jRFcF0amQUOsDvltfJw7XCal8JdgPU\r\ng6TNC4Fy9XYv0OAHc3oDp3vl1Yj8/1qBg6Rc39kehmD5v8SKYmpE7yFKxDF1ol9D\r\nKDG/LvClSvnuVP0b4BWdBAA9aJSFtdNGgEvpEUqGkJ1osLVqCMvSYsUtHmapaX3h\r\niM9RbX38jsSgsl44Rar5Ioc7KXOOZFGfEKyyUqucYpjWCOXJELAVAzp7XTvA2q55\r\nu31hO0w8Yx4uEQKlmxDuZmxpMz4EWARyjHSAuDKEW1RJvUr6+5uA9qeOKxLiKN1j\r\no6eWAcl6Wr9MreXR9kFpS6kHllfdVSrJES4ST0uh1Jp4EYgmiyMmFCbUpKXifpsN\r\nWCLDenE3hllF0+q3wIdu+4P82RIM71n7qVgnDnK29wnLhHDat9rkC62CIbonpkVY\r\nmnReX0jze+7twRanJOMCJ+lFg16BDvBcG8u0n/wIDkHHitBI7bU1k6c6DydLQ+69\r\nh8SCo6sO9YuD+/3xAGKad4ImZ6vTwlB4zDCpu6YgQWocWRXE+VkOb+RBfvP755PU\r\naLfL63AFVlpOnEpIio5++UjNJRuPuAA=\r\n </ds:X509Certificate>\r\n </ds:X509Data>\r\n </ds:KeyInfo>\r\n <EncryptionMethod Algorithm=\"http://www.w3.org/2001/04/xmlenc#aes128-cbc\">\r\n <xenc:KeySize xmlns:xenc=\"http://www.w3.org/2001/04/xmlenc#\">128</xenc:KeySize>\r\n</EncryptionMethod>\r\n </KeyDescriptor>\r\n <ArtifactResolutionService index=\"0\" isDefault=\"true\" Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:SOAP\" Location=\"https://idp.ssocircle.com:443/sso/ArtifactResolver/metaAlias/publicidp\"/>\r\n <SingleLogoutService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect\" Location=\"https://idp.ssocircle.com:443/sso/IDPSloRedirect/metaAlias/publicidp\" ResponseLocation=\"https://idp.ssocircle.com:443/sso/IDPSloRedirect/metaAlias/publicidp\"/>\r\n <SingleLogoutService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST\" Location=\"https://idp.ssocircle.com:443/sso/IDPSloPost/metaAlias/publicidp\" ResponseLocation=\"https://idp.ssocircle.com:443/sso/IDPSloPost/metaAlias/publicidp\"/>\r\n <SingleLogoutService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:SOAP\" Location=\"https://idp.ssocircle.com:443/sso/IDPSloSoap/metaAlias/publicidp\"/>\r\n <ManageNameIDService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect\" Location=\"https://idp.ssocircle.com:443/sso/IDPMniRedirect/metaAlias/publicidp\" ResponseLocation=\"https://idp.ssocircle.com:443/sso/IDPMniRedirect/metaAlias/publicidp\"/>\r\n <ManageNameIDService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST\" Location=\"https://idp.ssocircle.com:443/sso/IDPMniPOST/metaAlias/publicidp\" ResponseLocation=\"https://idp.ssocircle.com:443/sso/IDPMniPOST/metaAlias/publicidp\"/>\r\n <ManageNameIDService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:SOAP\" Location=\"https://idp.ssocircle.com:443/sso/IDPMniSoap/metaAlias/publicidp\"/>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</NameIDFormat>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</NameIDFormat>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</NameIDFormat>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</NameIDFormat>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:kerberos</NameIDFormat>\r\n <SingleSignOnService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST\" Location=\"https://idp.ssocircle.com:443/sso/SSOPOST/metaAlias/publicidp\"/>\r\n <NameIDMappingService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:SOAP\" Location=\"https://idp.ssocircle.com:443/sso/NIMSoap/metaAlias/publicidp\"/>\r\n </IDPSSODescriptor>\r\n</EntityDescriptor>\r\n"
},
"sp": {
"activeKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCuVzyqFgMSyDANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDMwNDRaFw0yODA1\nMTExNDMwNDRaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDRu7/EI0BlNzMEBFVAcbx+lLos\nvzIWU+01dGTY8gBdhMQNYKZ92lMceo2CuVJ66cUURPym3i7nGGzoSnAxAre+0YIM\n+U0razrWtAUE735bkcqELZkOTZLelaoOztmWqRbe5OuEmpewH7cx+kNgcVjdctOG\ny3Q6x+I4qakY/9qhBQIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAAeViTvHOyQopWEi\nXOfI2Z9eukwrSknDwq/zscR0YxwwqDBMt/QdAODfSwAfnciiYLkmEjlozWRtOeN+\nqK7UFgP1bRl5qksrYX5S0z2iGJh0GvonLUt3e20Ssfl5tTEDDnAEUMLfBkyaxEHD\nRZ/nbTJ7VTeZOSyRoVn5XHhpuJ0B\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,7C8510E4CED17A9F\n\nSRYezKuY+AgM+gdiklVDBQ1ljeCFKnW3c5BM9sEyEOfkQm0zZx6fLr0afup0ToE4\niJGLxKw8swAnUAIjYda9wxqIEBb9mILyuRPevyfzmio2lE9KnARDEYRBqbwD9Lpd\nvwZKNGHHJbZAgcUNfhXiYakmx0cUyp8HeO3Vqa/0XMiI/HAdlJ/ruYeT4e2DSrz9\nORZA2S5OvNpRQeCVf26l6ODKXnkDL0t5fDVY4lAhaiyhZtoT0sADlPIERBw73kHm\nfGCTniY9qT0DT+R5Rqukk42mN2ij/cAr+kdV5colBi1fuN6d9gawCiH4zSb3LzHQ\n9ccSlz6iQV1Ty2cRuTkB3zWC6Oy4q0BRlXnVRFOnOfYJztO6c2hD3Q9NxkDAbcgR\nYWJWHpd0/HI8GyBpOG7hAS1l6aoleH30QCDOo7N2rFrTAaPC6g84oZOFSqkqvx4R\nKTbWRwgJsqVxM6GqV6H9x1LNn2CpBizdGnp8VvnIiYcEvItMJbT1C1yeIUPoDDU2\nCt0Jofw/dquXStHWftPFjpIqB+5Ou//HQ2VNzjbyThNWVGtjnEKwSiHacQLS1sB3\niqFtSN/VCpdOcRujEBba+x5vlc8XCV1qr6x1PbvfPZVjyFdSM6JQidr0uEeDGDW3\nTuYC1YgURN8zh0QF2lJIMX3xgbhr8HHNXv60ulcjeqYmna6VCS8AKJQgRTr4DGWt\nAfv9BFV943Yp3nHwPC7nYC4FvMxOn4qW4KrHRJl57zcY6VDL4J030CfmvLjqUbuT\nLYiQp/YgFlmoE4bcGuCiaRfUJZCwooPK2dQMoIvMZeVl9ExUGdXVMg==\n-----END RSA PRIVATE KEY-----"
},
"entityId": "cb-saml-sp2",
"signMetadata": true,
"signRequests": true,
"standbyKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCQqf5mvKPOpzANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDQ0NDZaFw0yODA1\nMTExNDQ0NDZaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCXJXpaDE6QmY9eN9pwcG8k/54a\nK9YLzRgln64hZ6mvdK+OIIBB5E2Pgenfc3Pi8pF0B9dGUbbNK8+8L6HcZRT/3aXM\nWlJsENJdMS13pnmSFimsTqoxYnayc2EaHULtvhMvLKf7UPRwX4jzxLanc6R4IcUL\nJZ/dg9gBT5KDlm164wIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAHDyh2B4AZ1C9LSi\ngis+sAiVJIzODsnKg8pIWGI7bcFUK+i/Vj7qlx09ZD/GbrQts87Yp4aq+5OqVqb5\nn6bS8DWB8jHCoHC5HACSBb3J7x/mC0PBsKXA9A8NSFzScErvfD/ACjWg3DJEghxn\nlqAVTm/DQX/t8kNTdrLdlzsYTuE0\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,393409C5B5DFA31D\n\nO40s+E7P75d8OOcfvE3HTNY8gsULhYk7SBdRw50ZklH5G/TZwCxxfoRfPiA4Q1Jf\nbpEHF8BzyLzjXZwYJT5UqaXW/3ozMj7BZ95UfCR0hrxMXQWq4Nak6gFyHh/1focS\nljzsLoBjyqjCc4BiFPD8uQHVGFv/PttCLydshnAVdSSrFLi0kVsFJMYOmL9ILG6l\nLd7Sb2ayD0/+1L0lLW8F6IbTtEYAwuA+mX25Imr9JMPKem1YwI1pqUHr8ifq0kd+\nJsoI4Q0Qf2CKv/nfZI5EjqJO34U5podj2zkqN1W3z7dzdTYNOmigq8XVrBiSmT8B\nlE7Ea1GDFol90AeF6ltJWEE6rM6kYzOoModXdK0ozEu4JNnBV/Fu81sOV9zHBs+9\nzqM7jCC16b6n5W2IKGad02GVCBKE0fmIEfhEUsTJw5UJLjNFYF2PkA13Y7jVGZMT\n38MfE3gWcYYOhXVPuMvJ1thXbjXEImg3yH+XHN3RMyups2B1s2JAXYVP2n5zI9pS\nY3Wt6iXAkKJ0Fiaa/myitUGtL1QvbhBOOfsw9HFuesxzJuKTJ7gqs0ceYwtpQ4X8\nwjk0HXz/riAb+BI6ImEd6H077e/U5u1c9WOdqAKEExAlXL8EhG5Azsj84cCAFuGl\n+T5XVBir0a1jUBQycnsinGZoy3lhE+92j8EhM4LgrDbzoqICVLrk1jX9FiDbcqzZ\nif87phEJmxz+ymCygUjzYohc0sIOwVcMl+s6Y+JsfSBDyg2XEIhzPPdGdgpCrxBg\nKEtaNgtbHXo7UOlN6voWliM14n1g13+xtUuX7hRve3Uy7MMwtuSVJA==\n-----END RSA PRIVATE KEY-----"
},
"wantAssertionsSigned": true
},
"user": {
"email": "EmailAddress",
"firstName": "Firstname",
"lastName": "Lastname",
"name": "UserID",
"ssoId": "UserID"
}
}
"allowSignUp": true,
"automatic": false,
"enabled": true,
"domain": "intland.com",
"idp": {
"entityId": "https://idp.ssocircle.com",
"url": "",
"xml": "<?xml version=\"1.0\" encoding=\"UTF-8\" standalone=\"yes\"?>\r\n<EntityDescriptor entityID=\"https://idp.ssocircle.com\" xmlns=\"urn:oasis:names:tc:SAML:2.0:metadata\">\r\n <IDPSSODescriptor WantAuthnRequestsSigned=\"false\" protocolSupportEnumeration=\"urn:oasis:names:tc:SAML:2.0:protocol\">\r\n <KeyDescriptor use=\"signing\">\r\n <ds:KeyInfo xmlns:ds=\"http://www.w3.org/2000/09/xmldsig#\">\r\n <ds:X509Data>\r\n <ds:X509Certificate>\r\nMIIEYzCCAkugAwIBAgIDIAZmMA0GCSqGSIb3DQEBCwUAMC4xCzAJBgNVBAYTAkRF\r\nMRIwEAYDVQQKDAlTU09DaXJjbGUxCzAJBgNVBAMMAkNBMB4XDTE2MDgwMzE1MDMy\r\nM1oXDTI2MDMwNDE1MDMyM1owPTELMAkGA1UEBhMCREUxEjAQBgNVBAoTCVNTT0Np\r\ncmNsZTEaMBgGA1UEAxMRaWRwLnNzb2NpcmNsZS5jb20wggEiMA0GCSqGSIb3DQEB\r\nAQUAA4IBDwAwggEKAoIBAQCAwWJyOYhYmWZF2TJvm1VyZccs3ZJ0TsNcoazr2pTW\r\ncY8WTRbIV9d06zYjngvWibyiylewGXcYONB106ZNUdNgrmFd5194Wsyx6bPvnjZE\r\nERny9LOfuwQaqDYeKhI6c+veXApnOfsY26u9Lqb9sga9JnCkUGRaoVrAVM3yfghv\r\n/Cg/QEg+I6SVES75tKdcLDTt/FwmAYDEBV8l52bcMDNF+JWtAuetI9/dWCBe9VTC\r\nasAr2Fxw1ZYTAiqGI9sW4kWS2ApedbqsgH3qqMlPA7tg9iKy8Yw/deEn0qQIx8Gl\r\nVnQFpDgzG9k+jwBoebAYfGvMcO/BDXD2pbWTN+DvbURlAgMBAAGjezB5MAkGA1Ud\r\nEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmlj\r\nYXRlMB0GA1UdDgQWBBQhAmCewE7aonAvyJfjImCRZDtccTAfBgNVHSMEGDAWgBTA\r\n1nEA+0za6ppLItkOX5yEp8cQaTANBgkqhkiG9w0BAQsFAAOCAgEAAhC5/WsF9ztJ\r\nHgo+x9KV9bqVS0MmsgpG26yOAqFYwOSPmUuYmJmHgmKGjKrj1fdCINtzcBHFFBC1\r\nmaGJ33lMk2bM2THx22/O93f4RFnFab7t23jRFcF0amQUOsDvltfJw7XCal8JdgPU\r\ng6TNC4Fy9XYv0OAHc3oDp3vl1Yj8/1qBg6Rc39kehmD5v8SKYmpE7yFKxDF1ol9D\r\nKDG/LvClSvnuVP0b4BWdBAA9aJSFtdNGgEvpEUqGkJ1osLVqCMvSYsUtHmapaX3h\r\niM9RbX38jsSgsl44Rar5Ioc7KXOOZFGfEKyyUqucYpjWCOXJELAVAzp7XTvA2q55\r\nu31hO0w8Yx4uEQKlmxDuZmxpMz4EWARyjHSAuDKEW1RJvUr6+5uA9qeOKxLiKN1j\r\no6eWAcl6Wr9MreXR9kFpS6kHllfdVSrJES4ST0uh1Jp4EYgmiyMmFCbUpKXifpsN\r\nWCLDenE3hllF0+q3wIdu+4P82RIM71n7qVgnDnK29wnLhHDat9rkC62CIbonpkVY\r\nmnReX0jze+7twRanJOMCJ+lFg16BDvBcG8u0n/wIDkHHitBI7bU1k6c6DydLQ+69\r\nh8SCo6sO9YuD+/3xAGKad4ImZ6vTwlB4zDCpu6YgQWocWRXE+VkOb+RBfvP755PU\r\naLfL63AFVlpOnEpIio5++UjNJRuPuAA=\r\n </ds:X509Certificate>\r\n </ds:X509Data>\r\n </ds:KeyInfo>\r\n </KeyDescriptor>\r\n <KeyDescriptor use=\"encryption\">\r\n <ds:KeyInfo xmlns:ds=\"http://www.w3.org/2000/09/xmldsig#\">\r\n <ds:X509Data>\r\n <ds:X509Certificate>\r\nMIIEYzCCAkugAwIBAgIDIAZmMA0GCSqGSIb3DQEBCwUAMC4xCzAJBgNVBAYTAkRF\r\nMRIwEAYDVQQKDAlTU09DaXJjbGUxCzAJBgNVBAMMAkNBMB4XDTE2MDgwMzE1MDMy\r\nM1oXDTI2MDMwNDE1MDMyM1owPTELMAkGA1UEBhMCREUxEjAQBgNVBAoTCVNTT0Np\r\ncmNsZTEaMBgGA1UEAxMRaWRwLnNzb2NpcmNsZS5jb20wggEiMA0GCSqGSIb3DQEB\r\nAQUAA4IBDwAwggEKAoIBAQCAwWJyOYhYmWZF2TJvm1VyZccs3ZJ0TsNcoazr2pTW\r\ncY8WTRbIV9d06zYjngvWibyiylewGXcYONB106ZNUdNgrmFd5194Wsyx6bPvnjZE\r\nERny9LOfuwQaqDYeKhI6c+veXApnOfsY26u9Lqb9sga9JnCkUGRaoVrAVM3yfghv\r\n/Cg/QEg+I6SVES75tKdcLDTt/FwmAYDEBV8l52bcMDNF+JWtAuetI9/dWCBe9VTC\r\nasAr2Fxw1ZYTAiqGI9sW4kWS2ApedbqsgH3qqMlPA7tg9iKy8Yw/deEn0qQIx8Gl\r\nVnQFpDgzG9k+jwBoebAYfGvMcO/BDXD2pbWTN+DvbURlAgMBAAGjezB5MAkGA1Ud\r\nEwQCMAAwLAYJYIZIAYb4QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmlj\r\nYXRlMB0GA1UdDgQWBBQhAmCewE7aonAvyJfjImCRZDtccTAfBgNVHSMEGDAWgBTA\r\n1nEA+0za6ppLItkOX5yEp8cQaTANBgkqhkiG9w0BAQsFAAOCAgEAAhC5/WsF9ztJ\r\nHgo+x9KV9bqVS0MmsgpG26yOAqFYwOSPmUuYmJmHgmKGjKrj1fdCINtzcBHFFBC1\r\nmaGJ33lMk2bM2THx22/O93f4RFnFab7t23jRFcF0amQUOsDvltfJw7XCal8JdgPU\r\ng6TNC4Fy9XYv0OAHc3oDp3vl1Yj8/1qBg6Rc39kehmD5v8SKYmpE7yFKxDF1ol9D\r\nKDG/LvClSvnuVP0b4BWdBAA9aJSFtdNGgEvpEUqGkJ1osLVqCMvSYsUtHmapaX3h\r\niM9RbX38jsSgsl44Rar5Ioc7KXOOZFGfEKyyUqucYpjWCOXJELAVAzp7XTvA2q55\r\nu31hO0w8Yx4uEQKlmxDuZmxpMz4EWARyjHSAuDKEW1RJvUr6+5uA9qeOKxLiKN1j\r\no6eWAcl6Wr9MreXR9kFpS6kHllfdVSrJES4ST0uh1Jp4EYgmiyMmFCbUpKXifpsN\r\nWCLDenE3hllF0+q3wIdu+4P82RIM71n7qVgnDnK29wnLhHDat9rkC62CIbonpkVY\r\nmnReX0jze+7twRanJOMCJ+lFg16BDvBcG8u0n/wIDkHHitBI7bU1k6c6DydLQ+69\r\nh8SCo6sO9YuD+/3xAGKad4ImZ6vTwlB4zDCpu6YgQWocWRXE+VkOb+RBfvP755PU\r\naLfL63AFVlpOnEpIio5++UjNJRuPuAA=\r\n </ds:X509Certificate>\r\n </ds:X509Data>\r\n </ds:KeyInfo>\r\n <EncryptionMethod Algorithm=\"http://www.w3.org/2001/04/xmlenc#aes128-cbc\">\r\n <xenc:KeySize xmlns:xenc=\"http://www.w3.org/2001/04/xmlenc#\">128</xenc:KeySize>\r\n</EncryptionMethod>\r\n </KeyDescriptor>\r\n <ArtifactResolutionService index=\"0\" isDefault=\"true\" Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:SOAP\" Location=\"https://idp.ssocircle.com:443/sso/ArtifactResolver/metaAlias/publicidp\"/>\r\n <SingleLogoutService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect\" Location=\"https://idp.ssocircle.com:443/sso/IDPSloRedirect/metaAlias/publicidp\" ResponseLocation=\"https://idp.ssocircle.com:443/sso/IDPSloRedirect/metaAlias/publicidp\"/>\r\n <SingleLogoutService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST\" Location=\"https://idp.ssocircle.com:443/sso/IDPSloPost/metaAlias/publicidp\" ResponseLocation=\"https://idp.ssocircle.com:443/sso/IDPSloPost/metaAlias/publicidp\"/>\r\n <SingleLogoutService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:SOAP\" Location=\"https://idp.ssocircle.com:443/sso/IDPSloSoap/metaAlias/publicidp\"/>\r\n <ManageNameIDService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect\" Location=\"https://idp.ssocircle.com:443/sso/IDPMniRedirect/metaAlias/publicidp\" ResponseLocation=\"https://idp.ssocircle.com:443/sso/IDPMniRedirect/metaAlias/publicidp\"/>\r\n <ManageNameIDService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST\" Location=\"https://idp.ssocircle.com:443/sso/IDPMniPOST/metaAlias/publicidp\" ResponseLocation=\"https://idp.ssocircle.com:443/sso/IDPMniPOST/metaAlias/publicidp\"/>\r\n <ManageNameIDService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:SOAP\" Location=\"https://idp.ssocircle.com:443/sso/IDPMniSoap/metaAlias/publicidp\"/>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</NameIDFormat>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:transient</NameIDFormat>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</NameIDFormat>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</NameIDFormat>\r\n <NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:kerberos</NameIDFormat>\r\n <SingleSignOnService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST\" Location=\"https://idp.ssocircle.com:443/sso/SSOPOST/metaAlias/publicidp\"/>\r\n <NameIDMappingService Binding=\"urn:oasis:names:tc:SAML:2.0:bindings:SOAP\" Location=\"https://idp.ssocircle.com:443/sso/NIMSoap/metaAlias/publicidp\"/>\r\n </IDPSSODescriptor>\r\n</EntityDescriptor>\r\n"
},
"sp": {
"activeKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCuVzyqFgMSyDANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDMwNDRaFw0yODA1\nMTExNDMwNDRaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDRu7/EI0BlNzMEBFVAcbx+lLos\nvzIWU+01dGTY8gBdhMQNYKZ92lMceo2CuVJ66cUURPym3i7nGGzoSnAxAre+0YIM\n+U0razrWtAUE735bkcqELZkOTZLelaoOztmWqRbe5OuEmpewH7cx+kNgcVjdctOG\ny3Q6x+I4qakY/9qhBQIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAAeViTvHOyQopWEi\nXOfI2Z9eukwrSknDwq/zscR0YxwwqDBMt/QdAODfSwAfnciiYLkmEjlozWRtOeN+\nqK7UFgP1bRl5qksrYX5S0z2iGJh0GvonLUt3e20Ssfl5tTEDDnAEUMLfBkyaxEHD\nRZ/nbTJ7VTeZOSyRoVn5XHhpuJ0B\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,7C8510E4CED17A9F\n\nSRYezKuY+AgM+gdiklVDBQ1ljeCFKnW3c5BM9sEyEOfkQm0zZx6fLr0afup0ToE4\niJGLxKw8swAnUAIjYda9wxqIEBb9mILyuRPevyfzmio2lE9KnARDEYRBqbwD9Lpd\nvwZKNGHHJbZAgcUNfhXiYakmx0cUyp8HeO3Vqa/0XMiI/HAdlJ/ruYeT4e2DSrz9\nORZA2S5OvNpRQeCVf26l6ODKXnkDL0t5fDVY4lAhaiyhZtoT0sADlPIERBw73kHm\nfGCTniY9qT0DT+R5Rqukk42mN2ij/cAr+kdV5colBi1fuN6d9gawCiH4zSb3LzHQ\n9ccSlz6iQV1Ty2cRuTkB3zWC6Oy4q0BRlXnVRFOnOfYJztO6c2hD3Q9NxkDAbcgR\nYWJWHpd0/HI8GyBpOG7hAS1l6aoleH30QCDOo7N2rFrTAaPC6g84oZOFSqkqvx4R\nKTbWRwgJsqVxM6GqV6H9x1LNn2CpBizdGnp8VvnIiYcEvItMJbT1C1yeIUPoDDU2\nCt0Jofw/dquXStHWftPFjpIqB+5Ou//HQ2VNzjbyThNWVGtjnEKwSiHacQLS1sB3\niqFtSN/VCpdOcRujEBba+x5vlc8XCV1qr6x1PbvfPZVjyFdSM6JQidr0uEeDGDW3\nTuYC1YgURN8zh0QF2lJIMX3xgbhr8HHNXv60ulcjeqYmna6VCS8AKJQgRTr4DGWt\nAfv9BFV943Yp3nHwPC7nYC4FvMxOn4qW4KrHRJl57zcY6VDL4J030CfmvLjqUbuT\nLYiQp/YgFlmoE4bcGuCiaRfUJZCwooPK2dQMoIvMZeVl9ExUGdXVMg==\n-----END RSA PRIVATE KEY-----"
},
"entityId": "cb-saml-sp2",
"signMetadata": true,
"signRequests": true,
"standbyKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCQqf5mvKPOpzANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDQ0NDZaFw0yODA1\nMTExNDQ0NDZaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCXJXpaDE6QmY9eN9pwcG8k/54a\nK9YLzRgln64hZ6mvdK+OIIBB5E2Pgenfc3Pi8pF0B9dGUbbNK8+8L6HcZRT/3aXM\nWlJsENJdMS13pnmSFimsTqoxYnayc2EaHULtvhMvLKf7UPRwX4jzxLanc6R4IcUL\nJZ/dg9gBT5KDlm164wIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAHDyh2B4AZ1C9LSi\ngis+sAiVJIzODsnKg8pIWGI7bcFUK+i/Vj7qlx09ZD/GbrQts87Yp4aq+5OqVqb5\nn6bS8DWB8jHCoHC5HACSBb3J7x/mC0PBsKXA9A8NSFzScErvfD/ACjWg3DJEghxn\nlqAVTm/DQX/t8kNTdrLdlzsYTuE0\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,393409C5B5DFA31D\n\nO40s+E7P75d8OOcfvE3HTNY8gsULhYk7SBdRw50ZklH5G/TZwCxxfoRfPiA4Q1Jf\nbpEHF8BzyLzjXZwYJT5UqaXW/3ozMj7BZ95UfCR0hrxMXQWq4Nak6gFyHh/1focS\nljzsLoBjyqjCc4BiFPD8uQHVGFv/PttCLydshnAVdSSrFLi0kVsFJMYOmL9ILG6l\nLd7Sb2ayD0/+1L0lLW8F6IbTtEYAwuA+mX25Imr9JMPKem1YwI1pqUHr8ifq0kd+\nJsoI4Q0Qf2CKv/nfZI5EjqJO34U5podj2zkqN1W3z7dzdTYNOmigq8XVrBiSmT8B\nlE7Ea1GDFol90AeF6ltJWEE6rM6kYzOoModXdK0ozEu4JNnBV/Fu81sOV9zHBs+9\nzqM7jCC16b6n5W2IKGad02GVCBKE0fmIEfhEUsTJw5UJLjNFYF2PkA13Y7jVGZMT\n38MfE3gWcYYOhXVPuMvJ1thXbjXEImg3yH+XHN3RMyups2B1s2JAXYVP2n5zI9pS\nY3Wt6iXAkKJ0Fiaa/myitUGtL1QvbhBOOfsw9HFuesxzJuKTJ7gqs0ceYwtpQ4X8\nwjk0HXz/riAb+BI6ImEd6H077e/U5u1c9WOdqAKEExAlXL8EhG5Azsj84cCAFuGl\n+T5XVBir0a1jUBQycnsinGZoy3lhE+92j8EhM4LgrDbzoqICVLrk1jX9FiDbcqzZ\nif87phEJmxz+ymCygUjzYohc0sIOwVcMl+s6Y+JsfSBDyg2XEIhzPPdGdgpCrxBg\nKEtaNgtbHXo7UOlN6voWliM14n1g13+xtUuX7hRve3Uy7MMwtuSVJA==\n-----END RSA PRIVATE KEY-----"
},
"wantAssertionsSigned": true
},
"user": {
"email": "EmailAddress",
"firstName": "Firstname",
"lastName": "Lastname",
"name": "UserID",
"ssoId": "UserID"
}
}
SAML Service Provider example - ADFS
"saml": {
"allowSignUp": true,
"automatic": false,
"enabled": true,
"domain": "test.internal",
"idp": {
"entityId": "http://fs.codebeamer.com/adfs/services/trust",
"url": "https://adfs.codebeamer.com/FederationMetadata/2007-06/FederationMetadata.xml",
"xml": ""
},
"sp": {
"activeKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCuVzyqFgMSyDANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDMwNDRaFw0yODA1\nMTExNDMwNDRaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDRu7/EI0BlNzMEBFVAcbx+lLos\nvzIWU+01dGTY8gBdhMQNYKZ92lMceo2CuVJ66cUURPym3i7nGGzoSnAxAre+0YIM\n+U0razrWtAUE735bkcqELZkOTZLelaoOztmWqRbe5OuEmpewH7cx+kNgcVjdctOG\ny3Q6x+I4qakY/9qhBQIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAAeViTvHOyQopWEi\nXOfI2Z9eukwrSknDwq/zscR0YxwwqDBMt/QdAODfSwAfnciiYLkmEjlozWRtOeN+\nqK7UFgP1bRl5qksrYX5S0z2iGJh0GvonLUt3e20Ssfl5tTEDDnAEUMLfBkyaxEHD\nRZ/nbTJ7VTeZOSyRoVn5XHhpuJ0B\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,7C8510E4CED17A9F\n\nSRYezKuY+AgM+gdiklVDBQ1ljeCFKnW3c5BM9sEyEOfkQm0zZx6fLr0afup0ToE4\niJGLxKw8swAnUAIjYda9wxqIEBb9mILyuRPevyfzmio2lE9KnARDEYRBqbwD9Lpd\nvwZKNGHHJbZAgcUNfhXiYakmx0cUyp8HeO3Vqa/0XMiI/HAdlJ/ruYeT4e2DSrz9\nORZA2S5OvNpRQeCVf26l6ODKXnkDL0t5fDVY4lAhaiyhZtoT0sADlPIERBw73kHm\nfGCTniY9qT0DT+R5Rqukk42mN2ij/cAr+kdV5colBi1fuN6d9gawCiH4zSb3LzHQ\n9ccSlz6iQV1Ty2cRuTkB3zWC6Oy4q0BRlXnVRFOnOfYJztO6c2hD3Q9NxkDAbcgR\nYWJWHpd0/HI8GyBpOG7hAS1l6aoleH30QCDOo7N2rFrTAaPC6g84oZOFSqkqvx4R\nKTbWRwgJsqVxM6GqV6H9x1LNn2CpBizdGnp8VvnIiYcEvItMJbT1C1yeIUPoDDU2\nCt0Jofw/dquXStHWftPFjpIqB+5Ou//HQ2VNzjbyThNWVGtjnEKwSiHacQLS1sB3\niqFtSN/VCpdOcRujEBba+x5vlc8XCV1qr6x1PbvfPZVjyFdSM6JQidr0uEeDGDW3\nTuYC1YgURN8zh0QF2lJIMX3xgbhr8HHNXv60ulcjeqYmna6VCS8AKJQgRTr4DGWt\nAfv9BFV943Yp3nHwPC7nYC4FvMxOn4qW4KrHRJl57zcY6VDL4J030CfmvLjqUbuT\nLYiQp/YgFlmoE4bcGuCiaRfUJZCwooPK2dQMoIvMZeVl9ExUGdXVMg==\n-----END RSA PRIVATE KEY-----"
},
"entityId": "cb-saml-sp",
"signMetadata": true,
"signRequests": true,
"standbyKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCQqf5mvKPOpzANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDQ0NDZaFw0yODA1\nMTExNDQ0NDZaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCXJXpaDE6QmY9eN9pwcG8k/54a\nK9YLzRgln64hZ6mvdK+OIIBB5E2Pgenfc3Pi8pF0B9dGUbbNK8+8L6HcZRT/3aXM\nWlJsENJdMS13pnmSFimsTqoxYnayc2EaHULtvhMvLKf7UPRwX4jzxLanc6R4IcUL\nJZ/dg9gBT5KDlm164wIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAHDyh2B4AZ1C9LSi\ngis+sAiVJIzODsnKg8pIWGI7bcFUK+i/Vj7qlx09ZD/GbrQts87Yp4aq+5OqVqb5\nn6bS8DWB8jHCoHC5HACSBb3J7x/mC0PBsKXA9A8NSFzScErvfD/ACjWg3DJEghxn\nlqAVTm/DQX/t8kNTdrLdlzsYTuE0\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,393409C5B5DFA31D\n\nO40s+E7P75d8OOcfvE3HTNY8gsULhYk7SBdRw50ZklH5G/TZwCxxfoRfPiA4Q1Jf\nbpEHF8BzyLzjXZwYJT5UqaXW/3ozMj7BZ95UfCR0hrxMXQWq4Nak6gFyHh/1focS\nljzsLoBjyqjCc4BiFPD8uQHVGFv/PttCLydshnAVdSSrFLi0kVsFJMYOmL9ILG6l\nLd7Sb2ayD0/+1L0lLW8F6IbTtEYAwuA+mX25Imr9JMPKem1YwI1pqUHr8ifq0kd+\nJsoI4Q0Qf2CKv/nfZI5EjqJO34U5podj2zkqN1W3z7dzdTYNOmigq8XVrBiSmT8B\nlE7Ea1GDFol90AeF6ltJWEE6rM6kYzOoModXdK0ozEu4JNnBV/Fu81sOV9zHBs+9\nzqM7jCC16b6n5W2IKGad02GVCBKE0fmIEfhEUsTJw5UJLjNFYF2PkA13Y7jVGZMT\n38MfE3gWcYYOhXVPuMvJ1thXbjXEImg3yH+XHN3RMyups2B1s2JAXYVP2n5zI9pS\nY3Wt6iXAkKJ0Fiaa/myitUGtL1QvbhBOOfsw9HFuesxzJuKTJ7gqs0ceYwtpQ4X8\nwjk0HXz/riAb+BI6ImEd6H077e/U5u1c9WOdqAKEExAlXL8EhG5Azsj84cCAFuGl\n+T5XVBir0a1jUBQycnsinGZoy3lhE+92j8EhM4LgrDbzoqICVLrk1jX9FiDbcqzZ\nif87phEJmxz+ymCygUjzYohc0sIOwVcMl+s6Y+JsfSBDyg2XEIhzPPdGdgpCrxBg\nKEtaNgtbHXo7UOlN6voWliM14n1g13+xtUuX7hRve3Uy7MMwtuSVJA==\n-----END RSA PRIVATE KEY-----"
},
"wantAssertionsSigned": true
},
"user": {
"email": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"firstName": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname",
"lastName": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname",
"name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name",
"ssoId": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"
}
}
"allowSignUp": true,
"automatic": false,
"enabled": true,
"domain": "test.internal",
"idp": {
"entityId": "http://fs.codebeamer.com/adfs/services/trust",
"url": "https://adfs.codebeamer.com/FederationMetadata/2007-06/FederationMetadata.xml",
"xml": ""
},
"sp": {
"activeKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCuVzyqFgMSyDANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDMwNDRaFw0yODA1\nMTExNDMwNDRaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDRu7/EI0BlNzMEBFVAcbx+lLos\nvzIWU+01dGTY8gBdhMQNYKZ92lMceo2CuVJ66cUURPym3i7nGGzoSnAxAre+0YIM\n+U0razrWtAUE735bkcqELZkOTZLelaoOztmWqRbe5OuEmpewH7cx+kNgcVjdctOG\ny3Q6x+I4qakY/9qhBQIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAAeViTvHOyQopWEi\nXOfI2Z9eukwrSknDwq/zscR0YxwwqDBMt/QdAODfSwAfnciiYLkmEjlozWRtOeN+\nqK7UFgP1bRl5qksrYX5S0z2iGJh0GvonLUt3e20Ssfl5tTEDDnAEUMLfBkyaxEHD\nRZ/nbTJ7VTeZOSyRoVn5XHhpuJ0B\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,7C8510E4CED17A9F\n\nSRYezKuY+AgM+gdiklVDBQ1ljeCFKnW3c5BM9sEyEOfkQm0zZx6fLr0afup0ToE4\niJGLxKw8swAnUAIjYda9wxqIEBb9mILyuRPevyfzmio2lE9KnARDEYRBqbwD9Lpd\nvwZKNGHHJbZAgcUNfhXiYakmx0cUyp8HeO3Vqa/0XMiI/HAdlJ/ruYeT4e2DSrz9\nORZA2S5OvNpRQeCVf26l6ODKXnkDL0t5fDVY4lAhaiyhZtoT0sADlPIERBw73kHm\nfGCTniY9qT0DT+R5Rqukk42mN2ij/cAr+kdV5colBi1fuN6d9gawCiH4zSb3LzHQ\n9ccSlz6iQV1Ty2cRuTkB3zWC6Oy4q0BRlXnVRFOnOfYJztO6c2hD3Q9NxkDAbcgR\nYWJWHpd0/HI8GyBpOG7hAS1l6aoleH30QCDOo7N2rFrTAaPC6g84oZOFSqkqvx4R\nKTbWRwgJsqVxM6GqV6H9x1LNn2CpBizdGnp8VvnIiYcEvItMJbT1C1yeIUPoDDU2\nCt0Jofw/dquXStHWftPFjpIqB+5Ou//HQ2VNzjbyThNWVGtjnEKwSiHacQLS1sB3\niqFtSN/VCpdOcRujEBba+x5vlc8XCV1qr6x1PbvfPZVjyFdSM6JQidr0uEeDGDW3\nTuYC1YgURN8zh0QF2lJIMX3xgbhr8HHNXv60ulcjeqYmna6VCS8AKJQgRTr4DGWt\nAfv9BFV943Yp3nHwPC7nYC4FvMxOn4qW4KrHRJl57zcY6VDL4J030CfmvLjqUbuT\nLYiQp/YgFlmoE4bcGuCiaRfUJZCwooPK2dQMoIvMZeVl9ExUGdXVMg==\n-----END RSA PRIVATE KEY-----"
},
"entityId": "cb-saml-sp",
"signMetadata": true,
"signRequests": true,
"standbyKey": {
"certificate": "-----BEGIN CERTIFICATE-----\nMIICgTCCAeoCCQCQqf5mvKPOpzANBgkqhkiG9w0BAQsFADCBhDELMAkGA1UEBhMC\nVVMxEzARBgNVBAgMCldhc2hpbmd0b24xEjAQBgNVBAcMCVZhbmNvdXZlcjEdMBsG\nA1UECgwUU3ByaW5nIFNlY3VyaXR5IFNBTUwxCzAJBgNVBAsMAnNwMSAwHgYDVQQD\nDBdzcC5zcHJpbmcuc2VjdXJpdHkuc2FtbDAeFw0xODA1MTQxNDQ0NDZaFw0yODA1\nMTExNDQ0NDZaMIGEMQswCQYDVQQGEwJVUzETMBEGA1UECAwKV2FzaGluZ3RvbjES\nMBAGA1UEBwwJVmFuY291dmVyMR0wGwYDVQQKDBRTcHJpbmcgU2VjdXJpdHkgU0FN\nTDELMAkGA1UECwwCc3AxIDAeBgNVBAMMF3NwLnNwcmluZy5zZWN1cml0eS5zYW1s\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCXJXpaDE6QmY9eN9pwcG8k/54a\nK9YLzRgln64hZ6mvdK+OIIBB5E2Pgenfc3Pi8pF0B9dGUbbNK8+8L6HcZRT/3aXM\nWlJsENJdMS13pnmSFimsTqoxYnayc2EaHULtvhMvLKf7UPRwX4jzxLanc6R4IcUL\nJZ/dg9gBT5KDlm164wIDAQABMA0GCSqGSIb3DQEBCwUAA4GBAHDyh2B4AZ1C9LSi\ngis+sAiVJIzODsnKg8pIWGI7bcFUK+i/Vj7qlx09ZD/GbrQts87Yp4aq+5OqVqb5\nn6bS8DWB8jHCoHC5HACSBb3J7x/mC0PBsKXA9A8NSFzScErvfD/ACjWg3DJEghxn\nlqAVTm/DQX/t8kNTdrLdlzsYTuE0\n-----END CERTIFICATE-----",
"passphrase": "CB-ENCRYPTED-27-93-54-BA-39-B4-1-A1-49-E2-68-E0-C2-30-3D-70",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nProc-Type: 4,ENCRYPTED\nDEK-Info: DES-EDE3-CBC,393409C5B5DFA31D\n\nO40s+E7P75d8OOcfvE3HTNY8gsULhYk7SBdRw50ZklH5G/TZwCxxfoRfPiA4Q1Jf\nbpEHF8BzyLzjXZwYJT5UqaXW/3ozMj7BZ95UfCR0hrxMXQWq4Nak6gFyHh/1focS\nljzsLoBjyqjCc4BiFPD8uQHVGFv/PttCLydshnAVdSSrFLi0kVsFJMYOmL9ILG6l\nLd7Sb2ayD0/+1L0lLW8F6IbTtEYAwuA+mX25Imr9JMPKem1YwI1pqUHr8ifq0kd+\nJsoI4Q0Qf2CKv/nfZI5EjqJO34U5podj2zkqN1W3z7dzdTYNOmigq8XVrBiSmT8B\nlE7Ea1GDFol90AeF6ltJWEE6rM6kYzOoModXdK0ozEu4JNnBV/Fu81sOV9zHBs+9\nzqM7jCC16b6n5W2IKGad02GVCBKE0fmIEfhEUsTJw5UJLjNFYF2PkA13Y7jVGZMT\n38MfE3gWcYYOhXVPuMvJ1thXbjXEImg3yH+XHN3RMyups2B1s2JAXYVP2n5zI9pS\nY3Wt6iXAkKJ0Fiaa/myitUGtL1QvbhBOOfsw9HFuesxzJuKTJ7gqs0ceYwtpQ4X8\nwjk0HXz/riAb+BI6ImEd6H077e/U5u1c9WOdqAKEExAlXL8EhG5Azsj84cCAFuGl\n+T5XVBir0a1jUBQycnsinGZoy3lhE+92j8EhM4LgrDbzoqICVLrk1jX9FiDbcqzZ\nif87phEJmxz+ymCygUjzYohc0sIOwVcMl+s6Y+JsfSBDyg2XEIhzPPdGdgpCrxBg\nKEtaNgtbHXo7UOlN6voWliM14n1g13+xtUuX7hRve3Uy7MMwtuSVJA==\n-----END RSA PRIVATE KEY-----"
},
"wantAssertionsSigned": true
},
"user": {
"email": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"firstName": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname",
"lastName": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname",
"name": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name",
"ssoId": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"
}
}
Email domain configuration
Since 21.04-SP2 asterisk (*) is allowed as email domain, it will let users with any domain to log in via SSO.
Setup Codebeamer as service provider
Troubleshooting
For more information, visit SSO FAQ and Troubleshooting page.
Changes
Codebeamer 20.11
Since Codebeamer 20.11.LTSrelease the IDP's configuration is extended with the nameId option to configure an override for the IDP's nameID format property.
The accepted values:
• urn:oasis:names:tc:SAML:2.0:nameid-format:persistent
• urn:oasis:names:tc:SAML:2.0:nameid-format:transient
• urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
• urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified
• urn:oasis:names:tc:SAML:1.1:nameid-format:X509SubjectName
• urn:oasis:names:tc:SAML:1.1:nameid-format:WindowsDomainQualifiedName
• urn:oasis:names:tc:SAML:2.0:nameid-format:kerberos
• urn:oasis:names:tc:SAML:2.0:nameid-format:entity
 authentication via
authentication via