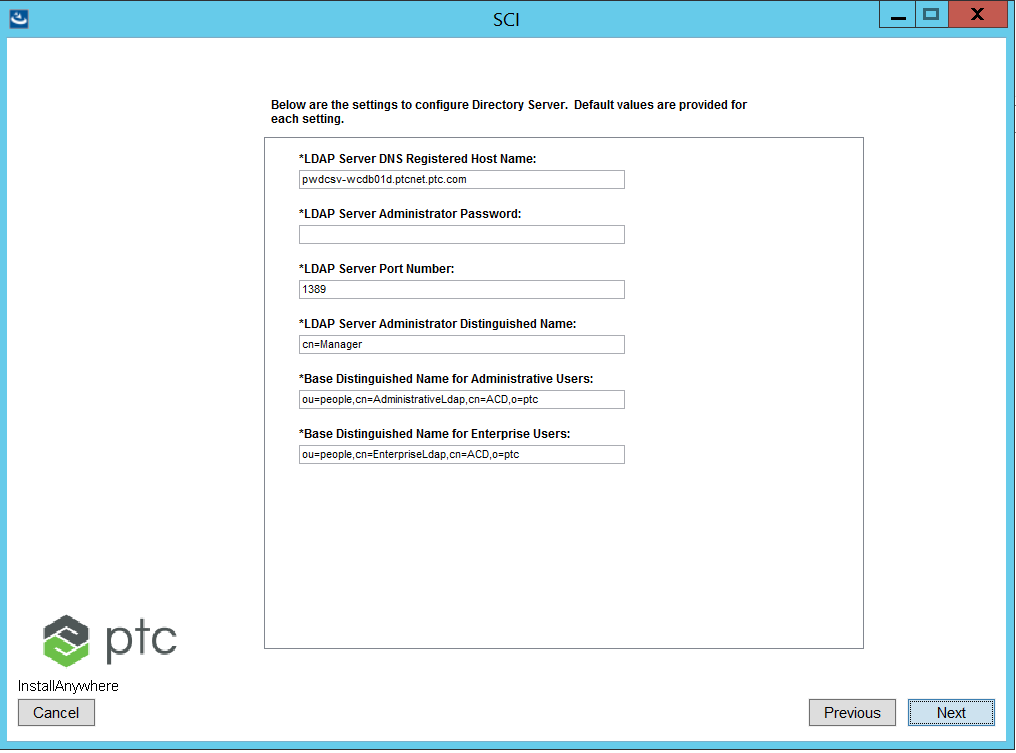
Entering Your LDAP Settings
It is recommended that you have a separate LDAP system for your Publisher and Viewer servers. If you use the same LDAP system for both servers, then any user is able to access the Task Manager. Having a separate LDAP system for your Publisher server enables you to restrict access to these programs.
If you must use the same LDAP system for the Publisher and Viewer servers, follow these steps to restrict access to Task Manager to a limited set of users:
1. Edit HOME>\SW\SW\System\WildFly\standalone\configuration\standalone-full-<database-name>.xml of the Publisher server.
2. Add a new security domain section with a new name. For example, InServiceTaskManager.
<security-domain name="InServiceTaskManager" cache-type="default"
<authentication>
<login-module code="com.ptc.sc.sce.user.SCEDefaultLoginModule" flag="optional"/>
<login-module code="org.jboss.security.auth.spi.LdapExtLoginModule" flag="sufficient"
<module-option name="java.naming.provider.url"
value="ldap://localhost.ptc.com:2389"/>
<module-option name="bindDN" value="cn=Manager"/>
<module-option name="bindCredential" value="admin"/>
<module-option name="baseCtxDN"
value="ou=people,cn=AdministrativeLdapTaskManager,cn=ACD,o=ptcrnd,o=ptc"/>
<module-option name="baseFilter" value="(uid={0})"/>
<module-option name="defaultRole" value="valid-user"/>
<module-option name="rolesCtxDN"
value="ou=people,cn=AdministrativeLdapTaskManager,cn=ACD,o=ptcrnd,o=ptc"/>
<module-option name="roleFilter" value="(member={1})"/>
<module-option name="roleAttributeID" value="cn"/>
</login-module
</authentication>
</security-domain>
<authentication>
<login-module code="com.ptc.sc.sce.user.SCEDefaultLoginModule" flag="optional"/>
<login-module code="org.jboss.security.auth.spi.LdapExtLoginModule" flag="sufficient"
<module-option name="java.naming.provider.url"
value="ldap://localhost.ptc.com:2389"/>
<module-option name="bindDN" value="cn=Manager"/>
<module-option name="bindCredential" value="admin"/>
<module-option name="baseCtxDN"
value="ou=people,cn=AdministrativeLdapTaskManager,cn=ACD,o=ptcrnd,o=ptc"/>
<module-option name="baseFilter" value="(uid={0})"/>
<module-option name="defaultRole" value="valid-user"/>
<module-option name="rolesCtxDN"
value="ou=people,cn=AdministrativeLdapTaskManager,cn=ACD,o=ptcrnd,o=ptc"/>
<module-option name="roleFilter" value="(member={1})"/>
<module-option name="roleAttributeID" value="cn"/>
</login-module
</authentication>
</security-domain>
3. Modify baseFilter module-option to define the LDAP group of users to give access to.
<module-option name="baseFilter" value="(&(sAMAccountName={0})
(memberOf=CN=Group01,CN=Users,DC=ad,DC=ptcnet,DC=com))"/>
(memberOf=CN=Group01,CN=Users,DC=ad,DC=ptcnet,DC=com))"/>
4. Edit <HOME>\SW\Config\System\Config\customizedContext_3.conf.xml and replace login.configuration.name property with the new security domain name created in step 2.
<Property Name="login.configuration.name" Value="InServiceTaskManager" />
5. Restart the services.
The LDAP settings create a default LDAP directory structure.
|
|
Depending on the product you are installing, the default LDAP directory structure is different.
|
Define the settings for the LDAP directory:
|
Option
|
Default
|
Entry
|
|---|---|---|
|
LDAP Server Administrative Password
|
administrator’s password
|
|
|
LDAP Server Port Number
|
1389
|
Define the port number that the LDAP Server listens on for requests.
|
|
LDAP Server Administrator Distinguished Name
|
cn=Manager
|
The distinguished name for the LDAP Server administrator. The setup program creates the directory using the distinguished name that you specify.
|
|
Base Distinguished Name for Administrative Users
|
Default values are taken from the configurations provided when configuring your Information Exchange Settings.
ou=people,
cn=AdministrativeLdap,
cn=PTC Arbortext Content Delivery_7.xx,
o=ptc
|
Define the distinguished name of the LDAP subtree under which Administrative LDAP entries reside. Users and groups under this subtree will be visible to PTC Arbortext Content Delivery.
You can edit this field to change the suggested name.
|
|
Base Distinguished Name for Enterprise Users
|
Default values are taken from the configurations provided when configuring your Information Exchange Settings.
ou=people,
cn=EnterpriseLdap,
cn=PTC Arbortext Content Delivery_7.xx,
o=ptc
|
Define the distinguished name of an LDAP subtree under which Enterprise LDAP entries reside. Users and groups under this subtree will be visible to PTC Arbortext Content Delivery. If a separate LDAP server such as Active Directory is to be used as the source of PTC Arbortext Content Delivery usernames and passwords, set this value to the location where PTC Arbortext Content Delivery users are located in this other LDAP server. If there are multiple branches in the LDAP, set the value to the base of all branches. The bind user (to be entered later) must have at least read permission to the location. For example:cn=Users,dc=atwood,dc=com
|
|
LDAP Server DNS Registered Host Name
|
<hostname>.<domain>
|
<hostname>.<domain> is the default.
|