Configuring the Central Authentication Server
For configuring PingFederate as the Central Authentication Server (CAS), and for installation and authorization processes, see Configuring the Central Auth Server. The following PTC Arbortext Content Delivery specific examples explain federated and delegated authentication:
• Federated Authentication Example: In the following example, ACD Applications (Task Manager, Configurator and Delivery) is the service provider, and PingFederate is the CAS. PTC Arbortext Content Delivery uses the open standard SAML 2.0 protocol for authentication exchange between the service provider and the identity provider.

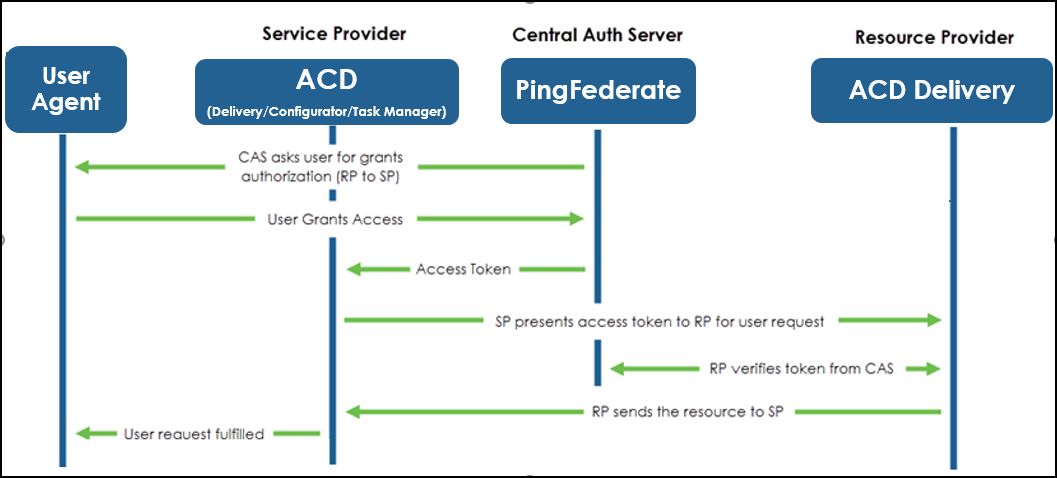
• Delegated Authentication Example: In the following example, ACD Task Manager is the service provider, PingFederate is the CAS, and ACD Delivery is the resource provider. ACD Task Manager uses the open standard OAuth2 protocol to authorize a service provider to access resources in a secure, reliable, and efficient manner.
Configuring Identity Providers
An Identity Providers (IdP) is an entity that authenticates a user or SAML subject, and transmits referential identity attributes based on that authentication to PingFederate.
For manually configuring third-party IdPs , see Configuring Authentication for Third-Party IdPs Manually and perform the following:
If you are deploying an IdP other than that used for the existing installation of your PTC product, PTC recommends that you review the user login attempt policies in the new IdP. The settings may be different from the policies that were used with your previously configured IdP. Review the policies in the new IdP to ensure that they match your security requirements.