GAS (Global Access Server) Enablement
|
|
In this topic, the version number 7.x for ThingWorx GAS includes v.7.0.0, v.7.0.1, and v.7.1.0. The version number 7.1.0 refers exclusively to v.7.1.0. For Axeda GAS, the specific starting version is 6.9.2.
|
The following sections describe changes to the ThingWorx products to support remote access. Click the title of a section to display its content. Click the title again to hide the content.
ThingWorx Global Access Server, v.7.1.x
The following figure illustrates the integration of the ThingWorx Global Access Server (GAS), v.7.1.x, in a ThingWorx environment.
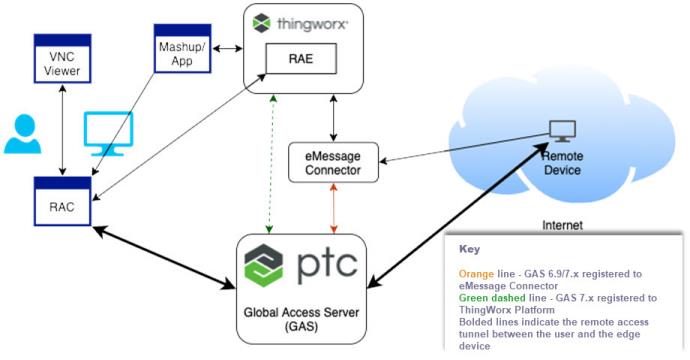
On the left is the end user setup, with the Remote Access Client (RAC) connected to a custom mashup or application that communicates with the ThingWorx Platform. Once a remote session is established, the end user can use a locally installed VNC Viewer, Axeda Desktop Viewer, or an SSH client to access the remote device. The remote device must be running the corresponding server for the remote session to work. For example, to use Axeda Desktop Viewer, the device running an eMessage Agent must be running Axeda Desktop Server. Similarly, to access a remote device using an SSH client, an SSH server must be running on the remote device along with the eMessage agent.
In the center are the ThingWorx Platform with the ThingWorx Remote Access Extension (RAE) installed, the eMessage Connector, and the Global Access Server (GAS). The eMessage agents can communicate directly with GAS or through the eMessage Connector to GAS. The RAE provides the Remote Access Subsystem that can communicate directly with GAS or with the eMessage Connector. It also provides all the entities with their properties and services that enable remote access for ThingWorx.
On the right is an edge device that is remotely accessible over the Internet. The RAC can establish a remote session with the device through the GAS or directly through ThingWorx Platform.
The features that have been added to ThingWorx Global Access Server (GAS) since v.6.9.2/v.6.9.3 of the Axeda Global Access Server follow:
• The GAS v.7.1.x can communicate directly with ThingWorx Platform, including sending current session counts and full audit records to the platform.
• When installing the GAS v.7.1.x, you have the choices illustrated in the following figure:
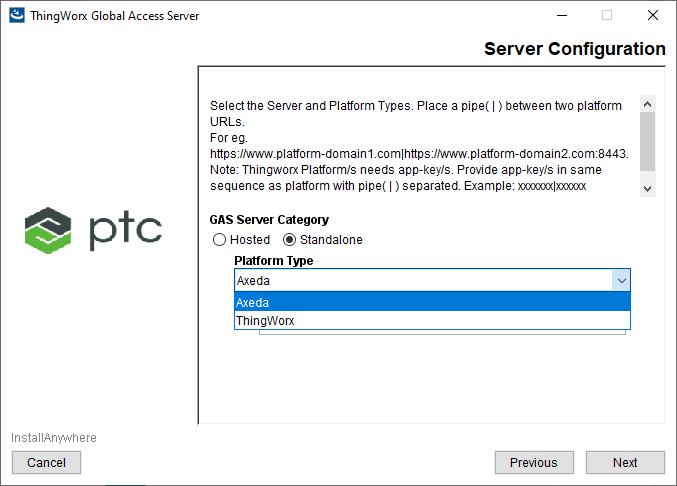
As shown in the figure above, you select the GAS Server Category as in previous releases of GAS, either of the following:
◦ Hosted, which means that PTC Cloud Services manages your Global Access Servers.
◦ Standalone, which means that you are managing your Global Access Servers.
The change here is that you also select the Platform Type, either of the following:
◦ Axeda, which means that you are running Axeda Global Access Server v.6.9.2 or v.6.9.3. It can also mean that you are running ThingWorx Global Access Server, v.7.x.x and want the GAS to communicate through the eMessage Connector. With this Platform Type, the GAS does not communicate directly with the Remote Access Subsystem or the Remote Access Extension.
◦ ThingWorx, which means that you are running ThingWorx Global Access Server, v.7.1.x and you want the GAS to communicate directly with the ThingWorx Platform instead of through the eMessage Connector. This means that the GAS can communicate directly with the Remote Access Subsystem and the Remote Access Extension.
• If eMessage Agents are configured to ask permission for a remote session from Policy Server, the agent sends a message to ThingWorx that permission is pending. The GAS does not start a remote session until the request is approved by a Policy Server application user.
As of v.7.1.0, Axeda Policy Server is rebranded as ThingWorx Policy Server. The information here applies to Axeda Policy Server v.7.0.0 and to ThingWorx Policy Server v.7.1.0. For simplicity, just "Policy Server" is used to refer to these two PTC products. |
• When a GAS registers for the first time, its status is set to "online". It goes offline only when the GAS unregisters. The GAS status must be "online" to use it for remote sessions (the online property value is true). In addition, the property, enabledForRemoteSessions property must be set to true. You can either set this property directly through ThingWorx Composer or run the EnableRemoteSessions service on the GAS Thing.
• When a GAS registers with the platform either directly or through the eMessage Connector, a GAS Thing is created with the name provided in the parameter, com.thingworx.gas.name, in the configuration file for the GAS, which is called RASConfig.properties.
• Remote sessions can be started and ended through the ThingWorx Platform rather than going through the eMessage Connector for Axeda assets.
• When GAS communicates directly with ThingWorx Platform and later unregisters, the GAS Thing is not deleted.
• If a GAS registers with an invalid token, the invalidToken property is set to true. The GAS messages will not be processed in the platform. Ensure that no attacker is trying to compromise your system once the token is set to invalid. Then, to reset or clear the token, use the service on the GAS Thing, called ClearToken.
Changes to the eMessage Connector for GAS Enablement
For the GAS enablement feature, the ThingWorx eMessage Connector will call the Remote Access Subsystem services for GAS, to register, unregister, and update the status of remote sessions.
The Remote Access Subsystem, the service, UnregisterExternalRemoteAccessServer, can be used to unregister a GAS from the ThingWorx Platform. Note that the service does not delete the GAS Thing. It just updates the online property of the Thing to false so that this GAS is ignored during GAS selection when a remote session is started.
ThingWorx Global Access Server, v.7.0.x
The following diagram illustrates the interactions of ThingWorx Global Access Server, v.7.0.x, with ThingWorx Platform:
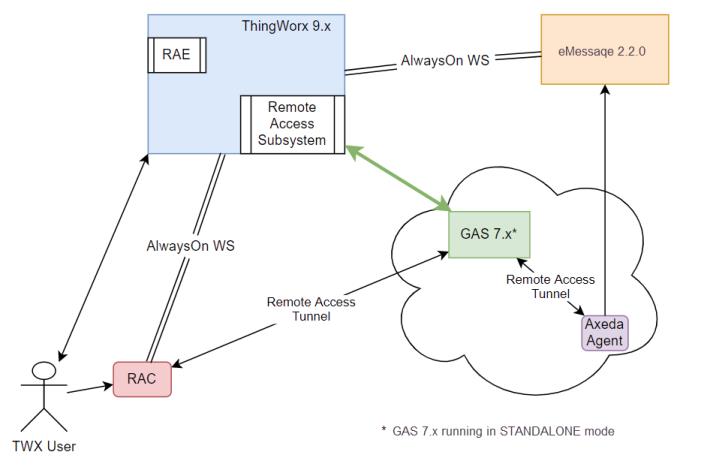
If you have been using the Axeda GAS Manager for your Axeda Global Access Servers and are switching to the ThingWorx Global Access Servers via a DNS switch, you must remove the old Axeda URL and IP references from GAS Manager. If you do not remove them, issues with GAS nodes connecting and disconnecting will arise. |
Axeda Global Access Server, v.6.9.2/v.6.9.3
The Axeda Global Access Server, v.6.9.2 and v.6.9.3 enable users to access Axeda eMessage Agents remotely through the ThingWorx eMessage Connector. Users can perform remote sessions using the ThingWorx Remote Access Client (RAC) and the user's preferred connection type, such as SSH or VNC/Axeda Desktop. The following figure illustrates the interactions of GAS v.6.9.2/v.6.9.3 with ThingWorx v.8.5.x and later

In this diagram are the ThingWorx Platform with the ThingWorx Remote Access Extension (RAE) and Remote Access Subsystem running, the eMessage Connector that communicates with remote Axeda agent assets, and the Axeda Global Access Server (GAS), v.6.9.2/v.6.9.3, which handles all activities related to establishing and ending remote sessions. Note that the Axeda GAS, v.6.9.2 and v.6.9.3, operates through the eMessage Connector only.
ThingWorx Remote Access Extension (RAE), v.3.0.0
The changes to the ThingWorx Remote Access Extension (RAE), v.3.0.0, include the following to support the ThingWorx Global Access Server (GAS), v.7.x:
• The RAE supports the use of ThingWorx Policy Server, v.7.x, for remote access. For details, refer to Remote Access: When Using Policy Server. The Remote Access Client, v.2.2.1, provides this support as well. You need to upgrade the RAE to v.3.0.0 in order to use Policy Server to control remote access to Axeda Agents.
• The RAE provides the following GAS-related services:
◦ RegisterExternalRemoteAccessServer — Allows a GAS to register itself directly with ThingWorx Platform.
◦ UnregisterExternalRemoteAccessServer — Allows a GAS to unregister itself or a user to unregister a GAS that is no longer needed.
◦ UpdateExternalRemoteAccessServerStatus — Allows a GAS to send status updates and audit records directly to ThingWorx Platform.
• All GAS-related entities that were previously provided in the Axeda Compatibility Extension have been migrated to the Remote Access Extension (RAE). Services that grant permissions and visibility in the ACE now call services in the RAE for permissions and visibility for remote access.
• The RAE provides the following permissions-related services on the RemoteAccessPermissionServices Thing:
◦ GrantPermissions — Called by the remote access permission/visibility granting services on the eMessagesServices Thing, this service grants common remote access permissions. This service is NOT intended to be called directly. This service takes the name of an organization, the name of a Thing Template or the name of a Thing, and the name of a user group as parameters.
◦ GrantPermissionsThingworxInternalForTemplate — This service should be run to support Always on Things, which include assets running an application written using a ThingWorx Edge SDK, a ThingWorx Edge MicroServer (EMS), or a Lua Script Resource (LSR). This service grants permissions to the specified organization, Thing Template, and user group. The RemoteAccessProvider for Things derived from the Thing Template is the ThingworxInternalRemoteAcessProvider.
◦ GrantPermissionsThingworxInternalForThing — This service should be run to support Always on Things, which include assets running an application written using a ThingWorx Edge SDK, a ThingWorx Edge MicroServer (EMS), or a Lua Script Resource (LSR). This service grants permissions to the specified organization, Thing, and user group. The RemoteAccessProvider for these Things is the ThingworxInternalRemoteAcessProvider. The Thing must implement the RemoteAccessible Thing Shape.
◦ GrantGlobalAccessServerPermissions — Grants permissions required for running a GAS to the specified organization and user group.
◦ GrantRemoteAccessPermissionsGAS — Grants remote access permissions for assets using remote sessions managed by a Global Access Server to the specified organization, user group, and Thing or Thing Template.
• The RAE, v.3.0.0, supports the GAS v.7.1 audit-message handling.
• The RAE, v.3.0.0, handles failover of the useInternalHostname flag to an external hostname.
ThingWorx Axeda Compatibility Extension (ACE), v.5.0.0
The changes to the Axeda Compatibility Extension (ACE), v.5.0.0, follow:
• All GAS-related entities that were previously provided in the Axeda Compatibility Extension have been moved to the Remote Access Extension (RAE).
• The Axeda.RemoteAccessible Thing Shape is no longer necessary so it too has been removed from the ACE. An existing Axeda.RemoteAccessible Thing Shape is migrated into the RAE GASRemoteAccessible ThingShape when you upgrade the extensions. The RemoteAccessible Thing Shape contains the information needed for all remote sessions while GASRemoteAccessible contains only the information needed for using GAS for remote sessions.
• Services of the ACE that grant permissions and visibility for the eMessage Connector have been rewritten to call related services that are now part of the RAE.
ThingWorx eMessage Connector, v.2.2.0
The changes to the ThingWorx eMessage Connector, v.2.2.0, to support the ThingWorx GAS v.7.x as well as the Axeda GAS v.6.9.2/v.6.9.3, follow:
• The eMessage-based audit workflows (Axeda GAS v.6.9.2/v.6.9.3 and GAS 7.x). The eMessage Connector now uses the same RemoteAccessSubsystem services to update status as used by ThingWorx GAS v.7.1.x.
• The workflows for GAS registration and un-registration use the RegisterExternalRemoteAccessServer and UnregisterExternalRemoteAccessServer services provided in RAE, v.3.0.0.